7 min to read
TryHackMe - Carnage - Write-Up

The TryHackMe room Carnage can be found here.
Eric Fischer from the Purchasing Department at Bartell Ltd has received an email from a known contact with a Word document attachment. Upon opening the document, he accidentally clicked on “Enable Content.” The SOC Department immediately received an alert from the endpoint agent that Eric’s workstation was making suspicious connections outbound. The pcap was retrieved from the network sensor and handed to you for analysis.
Today we some interesting work ahead of us: we’ll be looking at actual malicious traffic captured by a member of the InfoSec community.
As such, we should be very careful NOT to visit any of the addresses found in our investigation as they are known untrustworthy at best and outright malicious at worse.
Are you ready for the journey?
Let’s load the provided pcap file into Wireshark and get started!
What was the date and time for the first HTTP connection to the malicious IP?
(answer format: yyyy-mm-dd hh:mm:ss)
We can find the answer to this by simply filtering for http in Wireshark. Since we’re looking for the first connection, it’s the first packet that comes up.
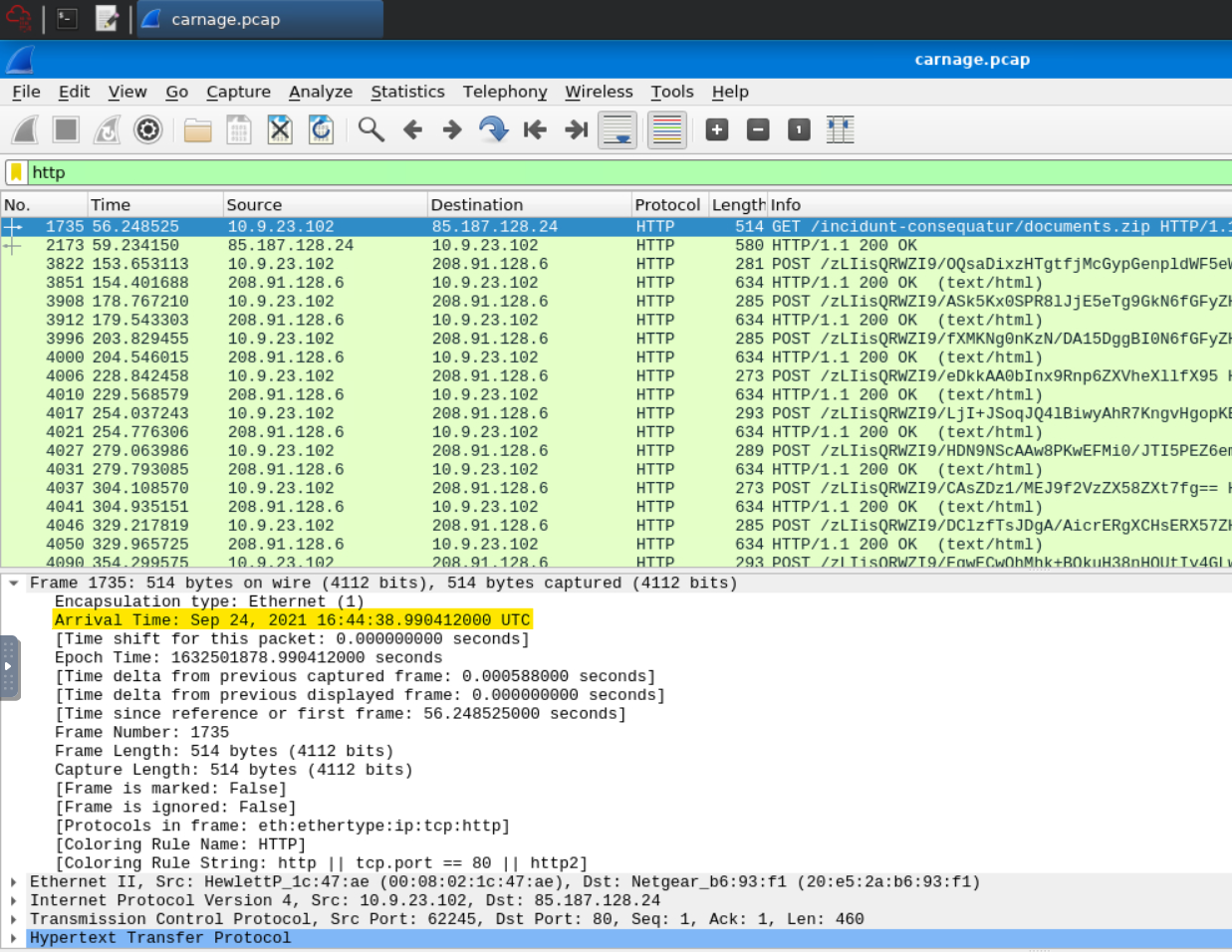
We then take the “Arrival Time” for this packet and format it to the question’s standard.
Answer: 2021-09-24 16:44:38
What is the name of the zip file that was downloaded?
This information is readily found in the info category for the packet.
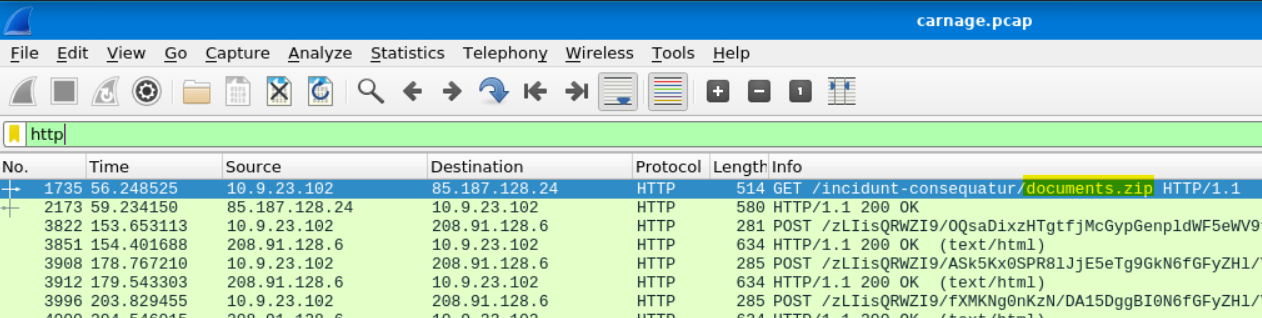
Answer: documents.zip
What was the domain hosting the malicious zip file?
The host domain is provided by the Hypertext Transfer Protocol section of the packet.
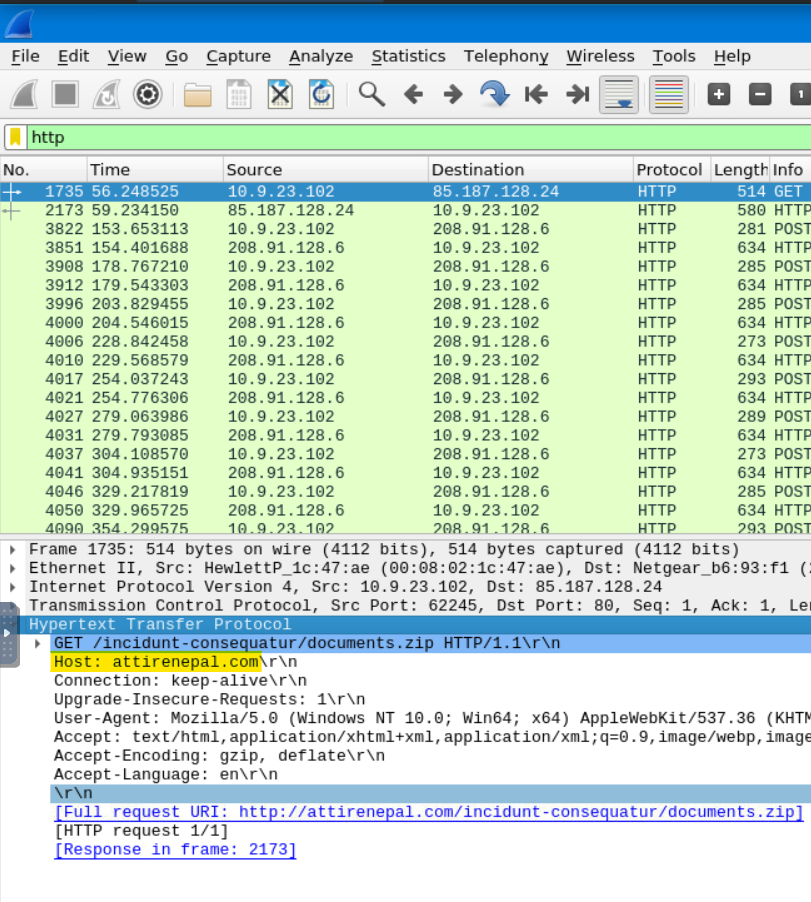
Answer: attirenepal.com
Without downloading the file, what is the name of the file in the zip file?
We can look for the file name by following the HTTP stream of the download request packet, as such:
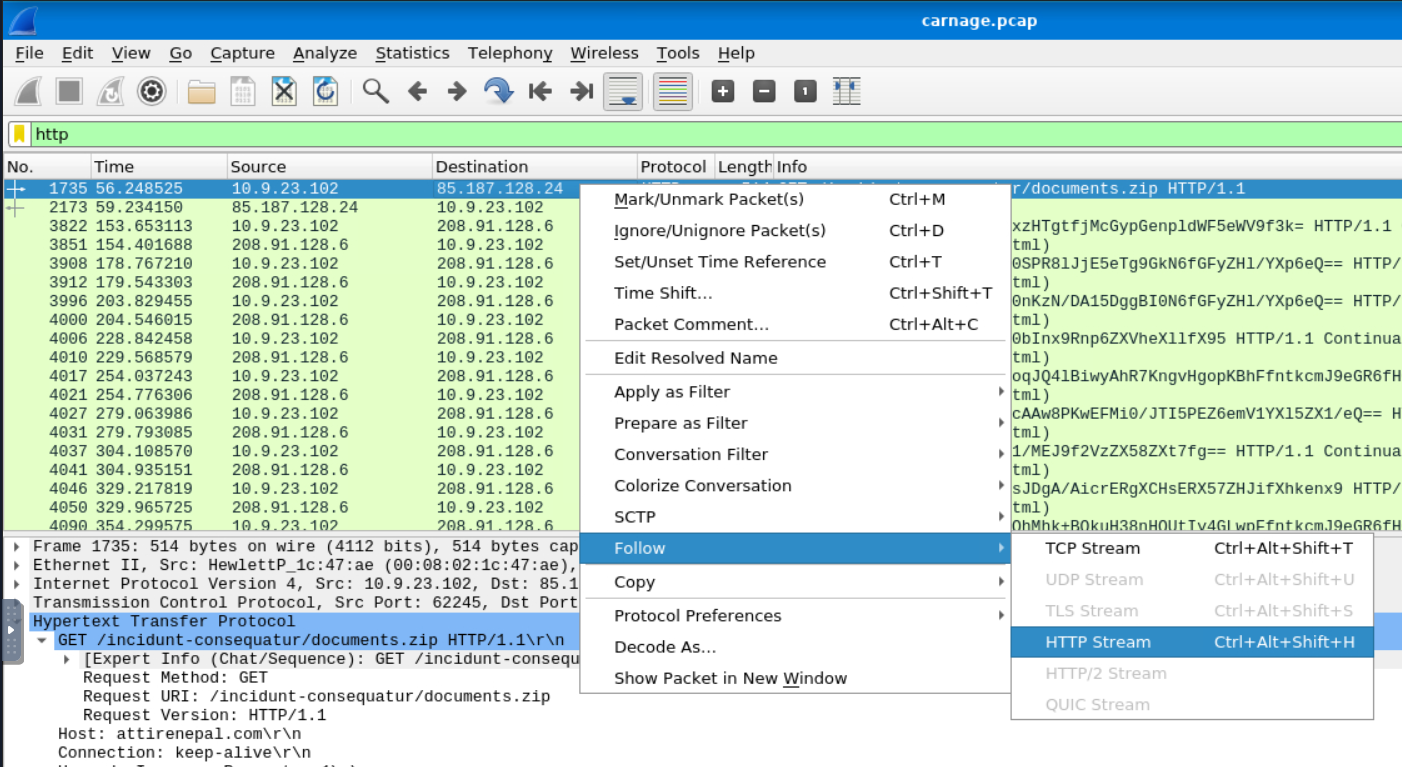
Opening this up, we can see a filename with an Excel extension buried among the noise. This is most likely our file.
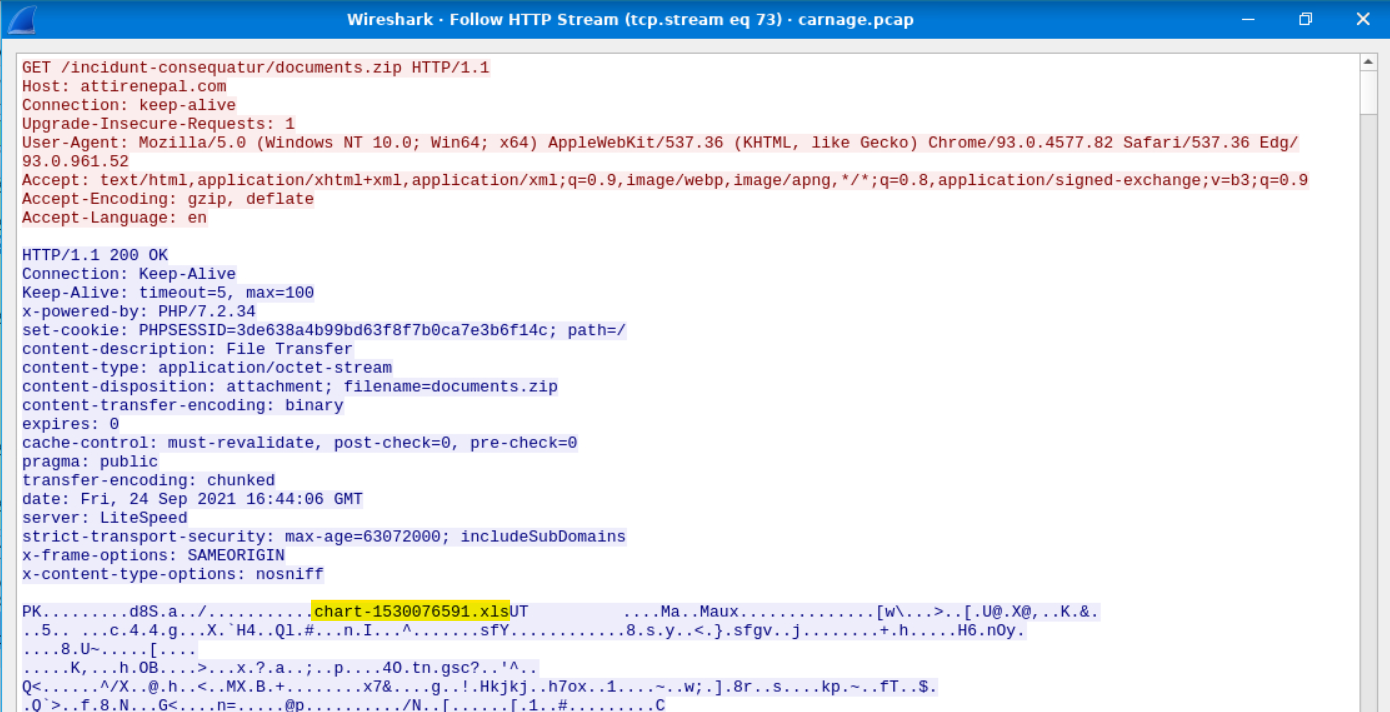
Answer: chart-1530076591.xls
What is the name of the webserver of the malicious IP from which the zip file was downloaded?
We can actually find the answer to the next two questions with this window as well.
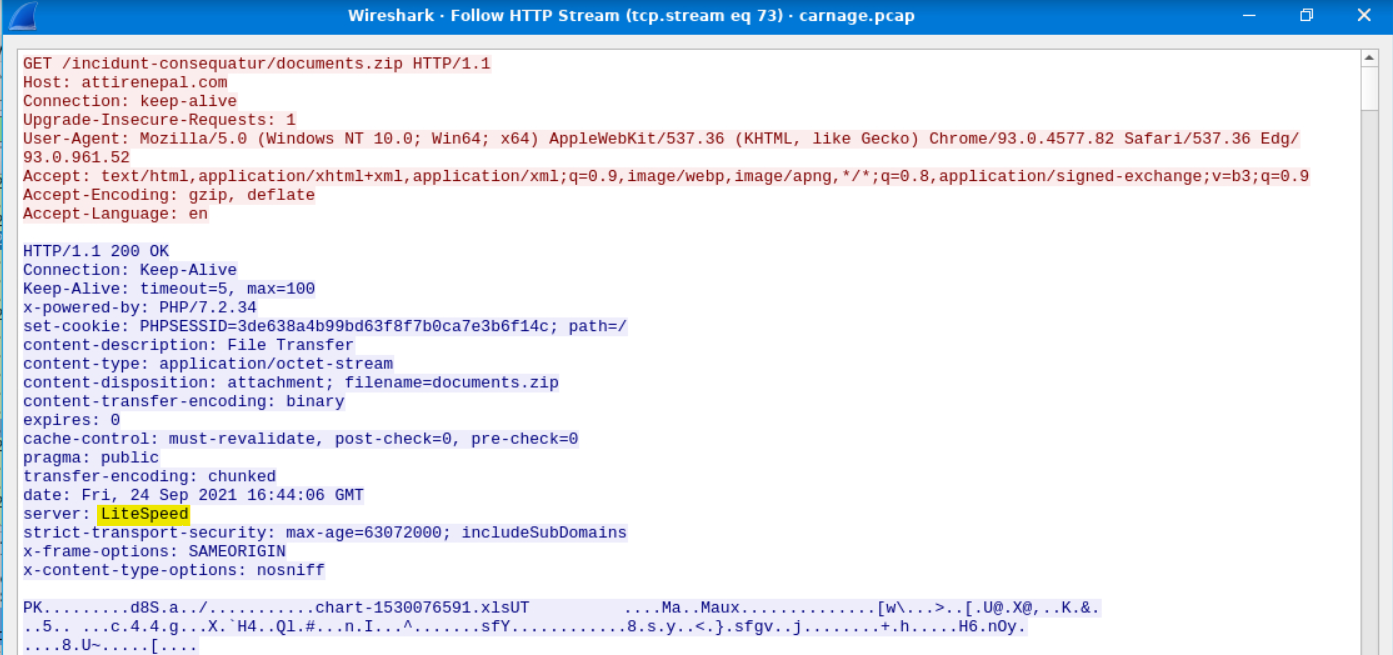
Answer: LiteSpeed
What is the version of the webserver from the previous question?
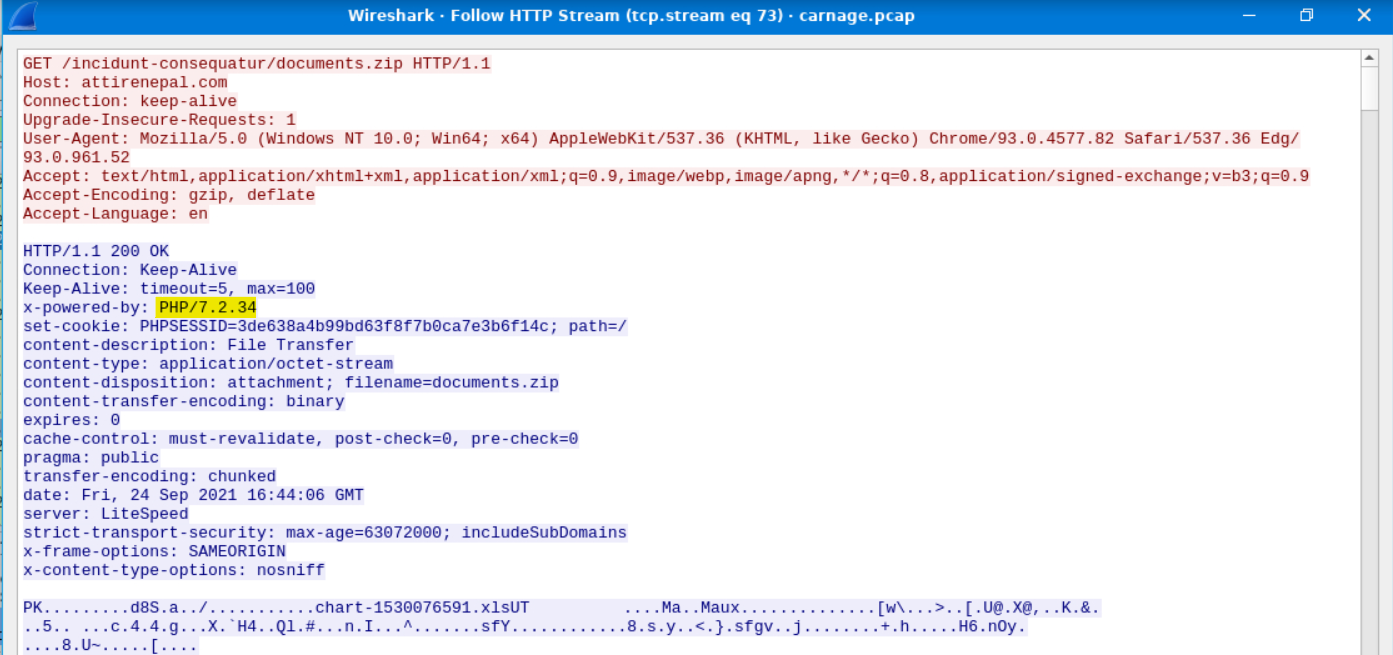
Answer: PHP/7.2.34
Malicious files were downloaded to the victim host from multiple domains. What were the three domains involved with this activity?
This took a second for me to determine what search parameters would return this information. The hint provided tells us to look in a very narrow time range, only 19 seconds. Combining the provided time frame with the knowledge that we were looking domain names, I crafted the below search:
dns and (frame.time >= "2021-09-24 16:45:11") && (frame.time <= "2021-09-24 16:45:30")
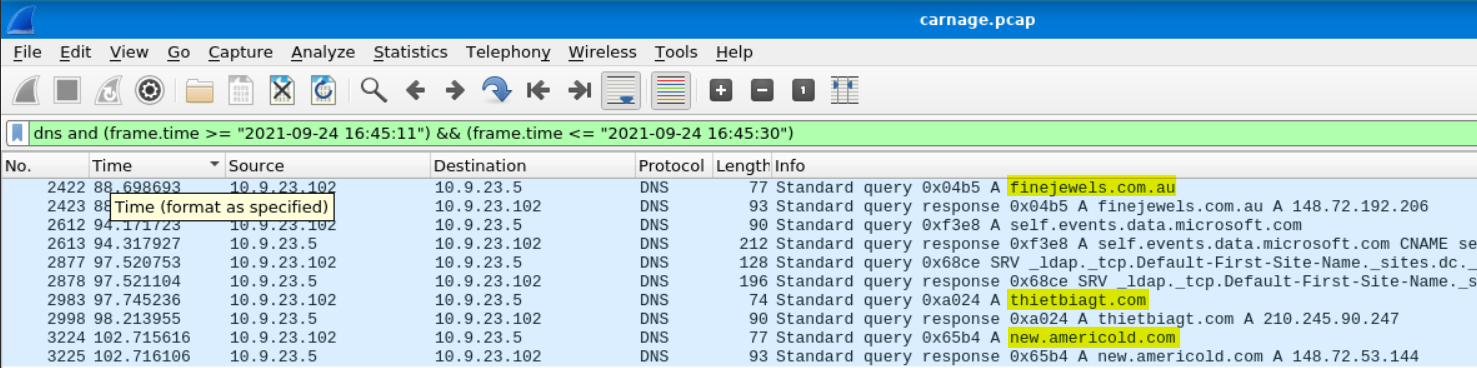
This sent back 10 frames, which include our answers.
Answer: finejewels.com.au, thietbiagt.com, new.americold.com
Which certificate authority issued the SSL certificate to the first domain from the previous question?
I found this by removing the dns filter from my search and and checking for the first TSL packet for finejewels.com.au.
I followed the TCP stream and found reference to the certificate authority in the results:
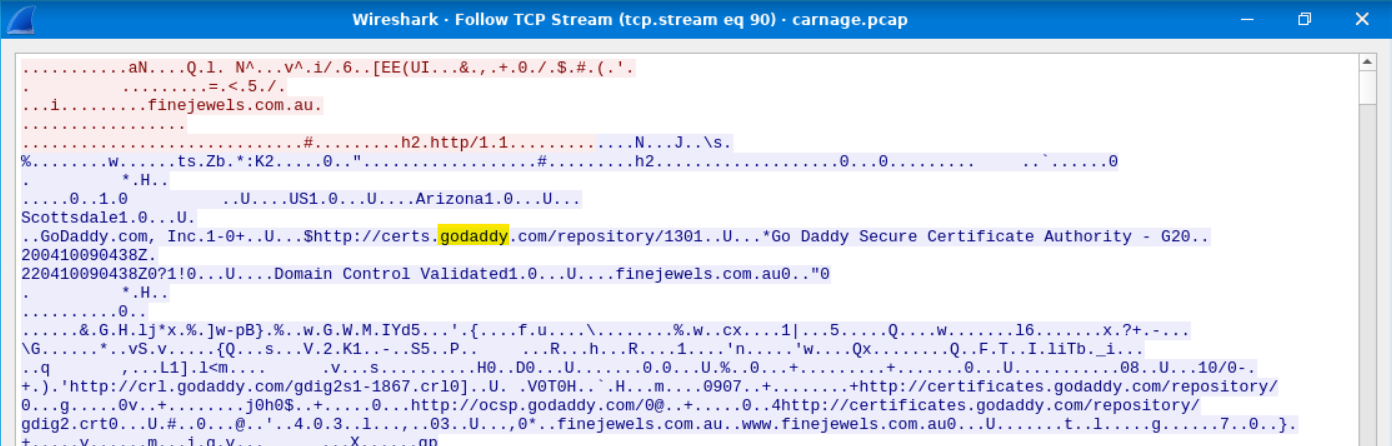
Answer: GoDaddy
What are the two IP addresses of the Cobalt Strike servers? Use VirusTotal (the Community tab) to confirm if IPs are identified as Cobalt Strike C2 servers. (answer format: enter the IP addresses in sequential order)
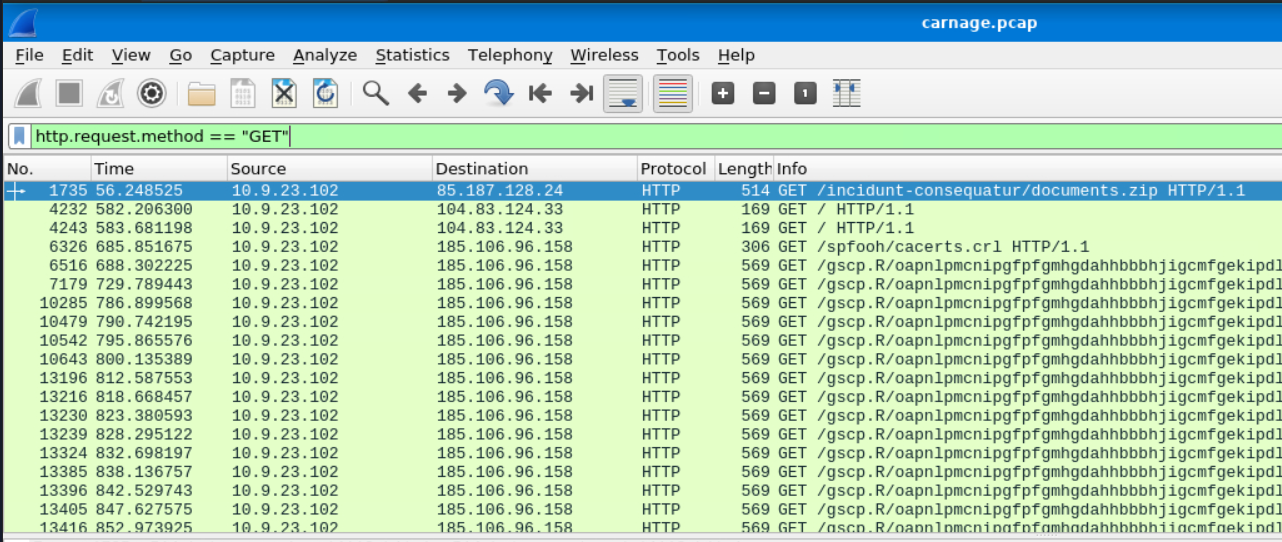
We’re looking for information on IP addresses that the affected machine is making regular contact with. We can begin our search by looking for GET requests by using the following filter: http.request.method == "GET".
We can go to Statistics -> Conversations to analyze the traffic more coherently.
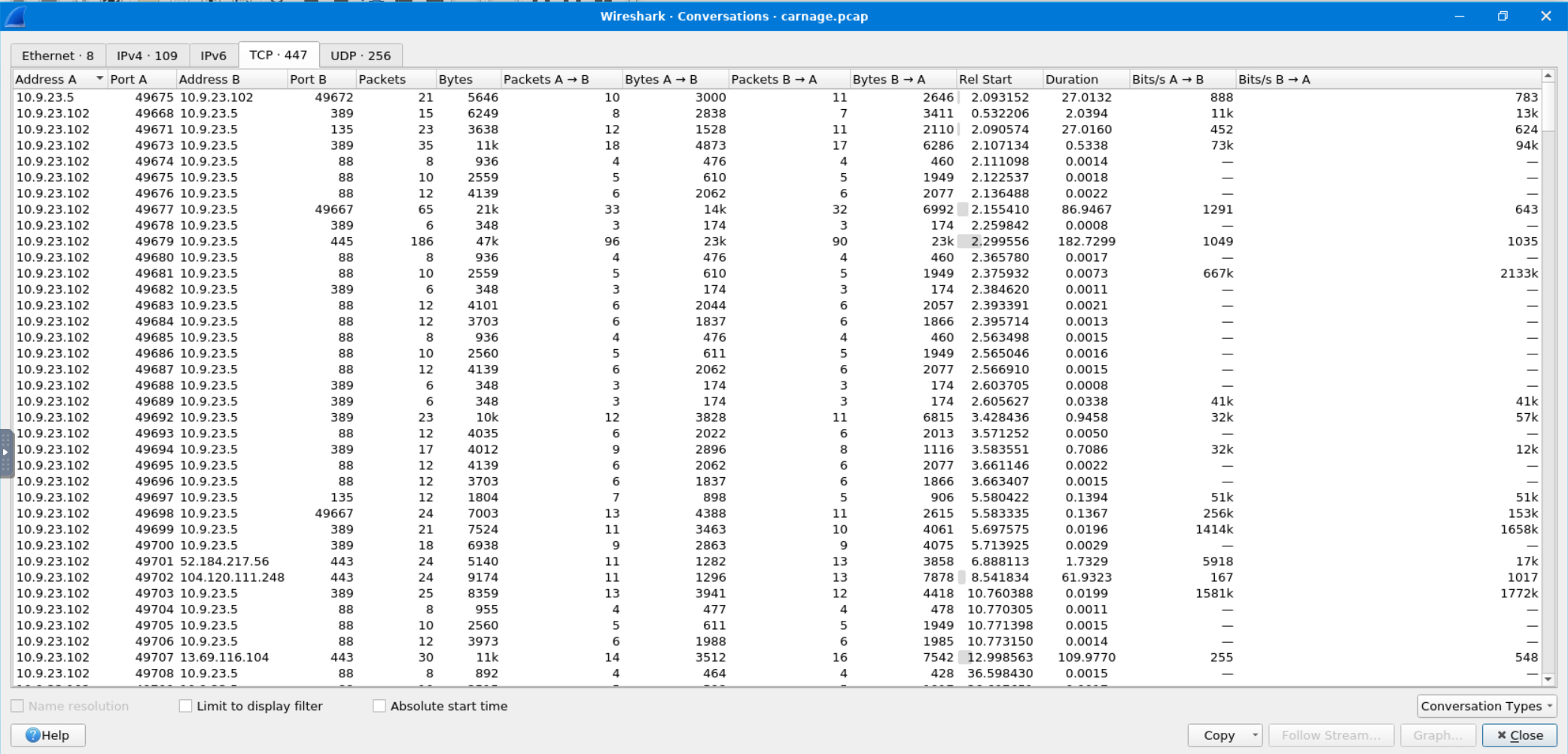
We see 10.9.23.102 communicating with a lot of other addresses, but we don’t know which are the C2 servers yet, so we’ll need to check each of them out. Anything with an address like 10.9.23.XXX can be presumed to be part of the same subnet and thus not our suspect C2s.
We take each IP address and run it through VirusTotal to see what the Community has come up with. After a bit of trial and error, we find the two addresses the question requests.
Answer: 185.106.96.158, 185.125.204.174
What is the Host header for the first Cobalt Strike IP address from the previous question?
This is found be following the TCP stream of one of the packets sent to the first IP address.
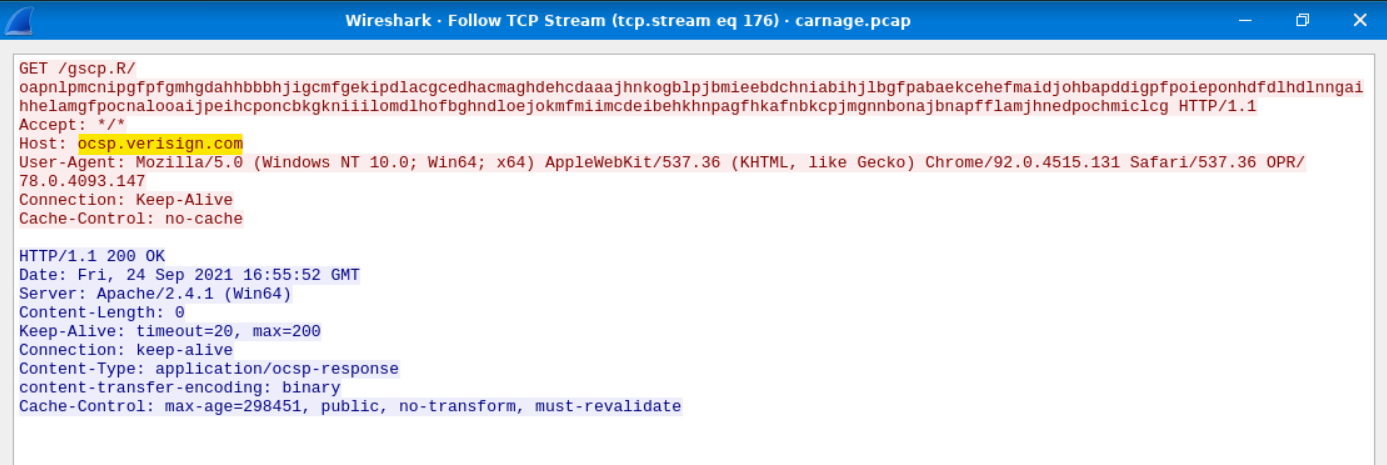
Answer: ocsp.verisign.com
What is the domain name for the first IP address of the Cobalt Strike server? You may use VirusTotal to confirm if it’s the Cobalt Strike server (check the Community tab).
We can find this in Wireshark by searching for the DNS A record for 185.106.96.158. The filter is as follows: dns.a == 185.106.96.158.
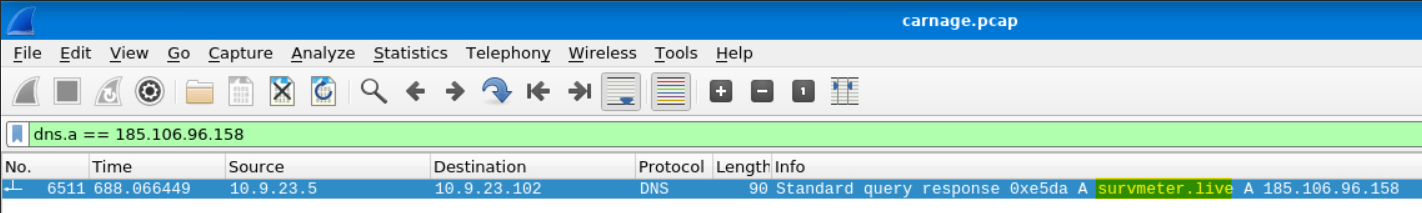
This domain name shows up for the IP address in VirusTotal under Relations.
Answer: survmeter.live
What is the domain name of the second Cobalt Strike server IP? You may use VirusTotal to confirm if it’s the Cobalt Strike server (check the Community tab).
Rinse and repeat the for the second.
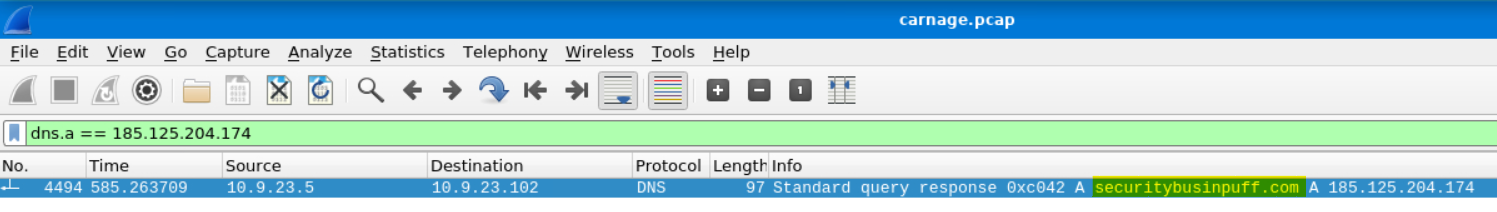
Again, we can confirm this in VirusTotal.
Answer: securitybusinpuff.com
What is the domain name of the post-infection traffic?
Looking for HTTP traffic after the time period in which the infection happened, we see many POST packets directed to one domain.
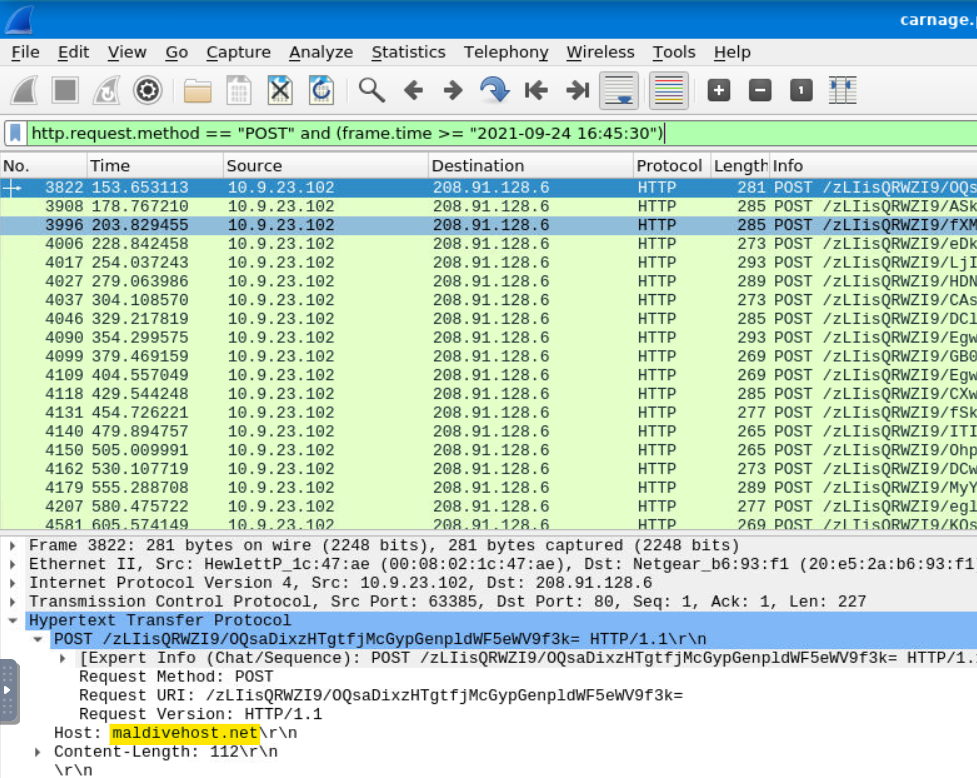
Answer: maldivehost.net
What are the first eleven characters that the victim host sends out to the malicious domain involved in the post-infection traffic?
Notice how every POST begins the same?
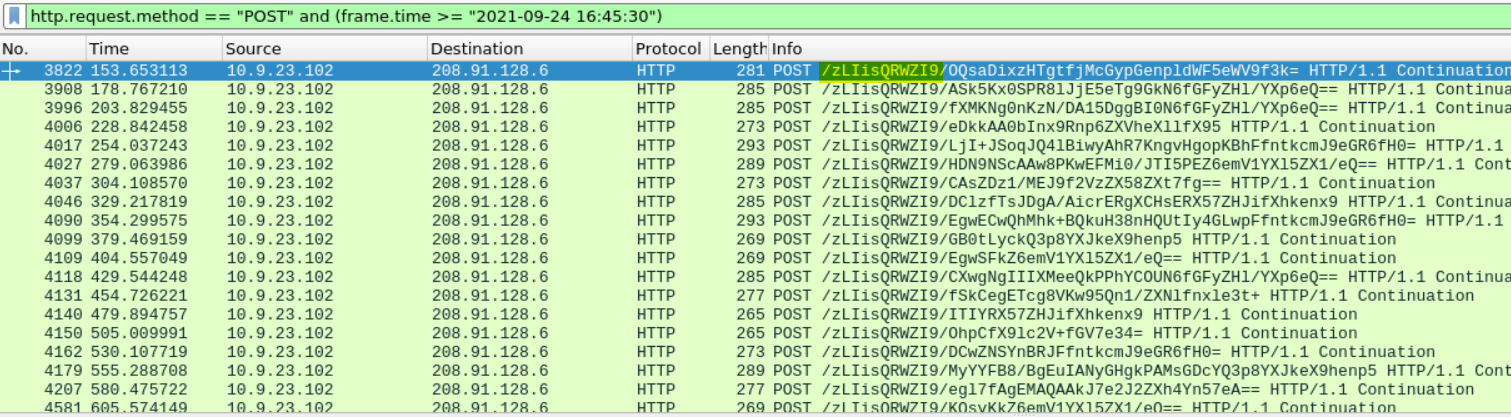
Answer: zLIisQRWZI9
What was the length for the first packet sent out to the C2 server?
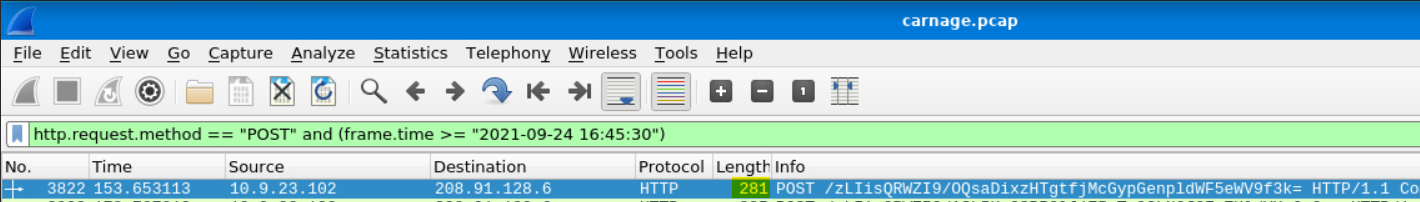
Answer: 281
What was the Server header for the malicious domain from the previous question?
We can follow the TCP stream for the previous packet to find this information.
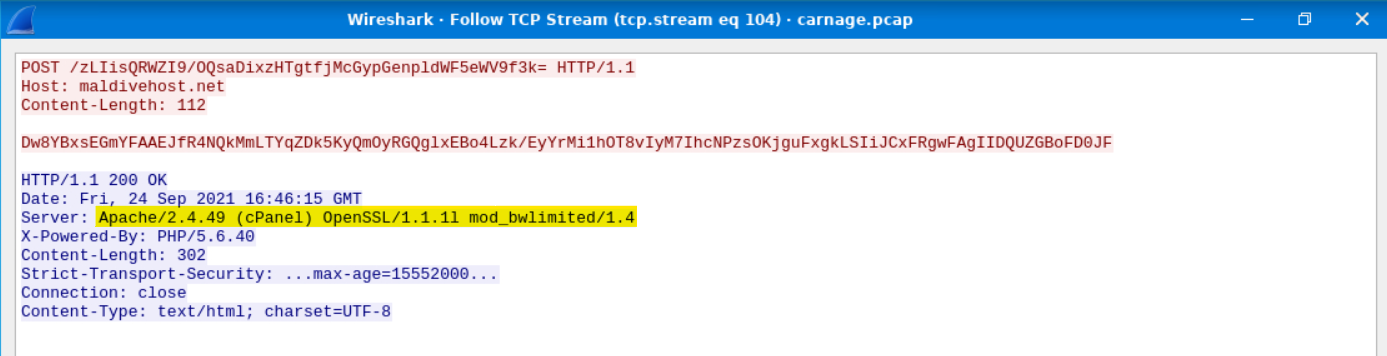
Answer: Apache/2.4.49 (cPanel) OpenSSL/1.1.1l mod_bwlimited/1.4
The malware used an API to check for the IP address of the victim’s machine. What was the date and time when the DNS query for the IP check domain occurred?
(answer format: yyyy-mm-dd hh:mm:ss UTC)
We can craft a filter that involves the victim’s IP address, DNS, and a search for “api” in the frame. The following does the trick: ip.addr == 10.9.23.102 and dns and frame contains "api".
After this we should look for a frame mentioning an API that appears to involve IP addresses. Then we need only check the time for the interaction and convert it to the desired format.
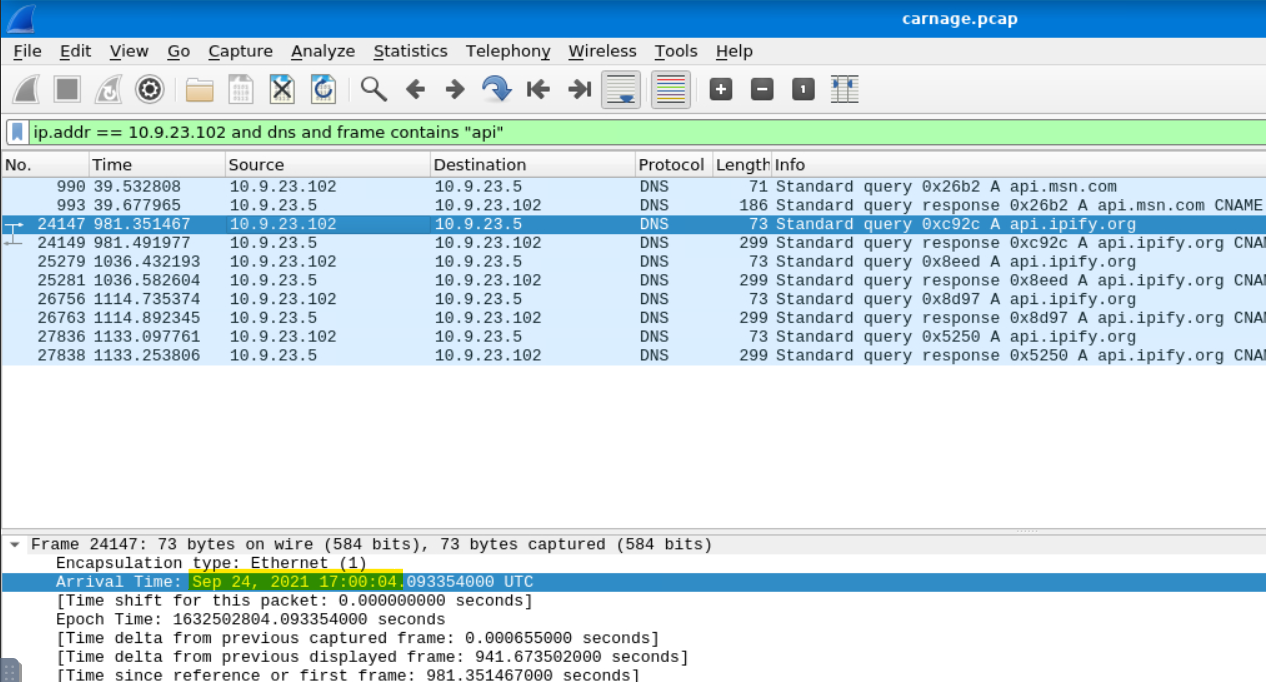
Answer: 2021-09-24 17:00:04
What was the domain in the DNS query from the previous question?
This is found from the previous query.
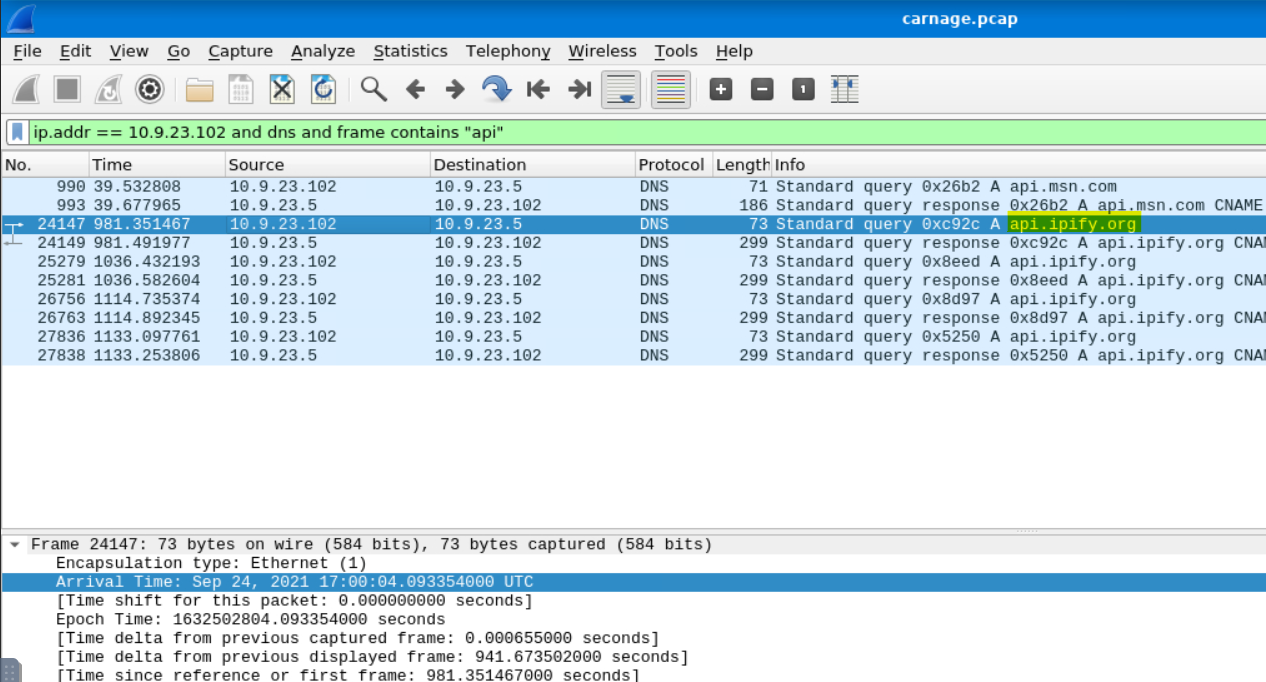
Answer: api.ipify.org
Looks like there was some malicious spam (malspam) activity going on. What was the first MAIL FROM address observed in the traffic?
We can find the first “MAIL FROM” by searching SMTP traffic: smtp.req.parameter contains FROM
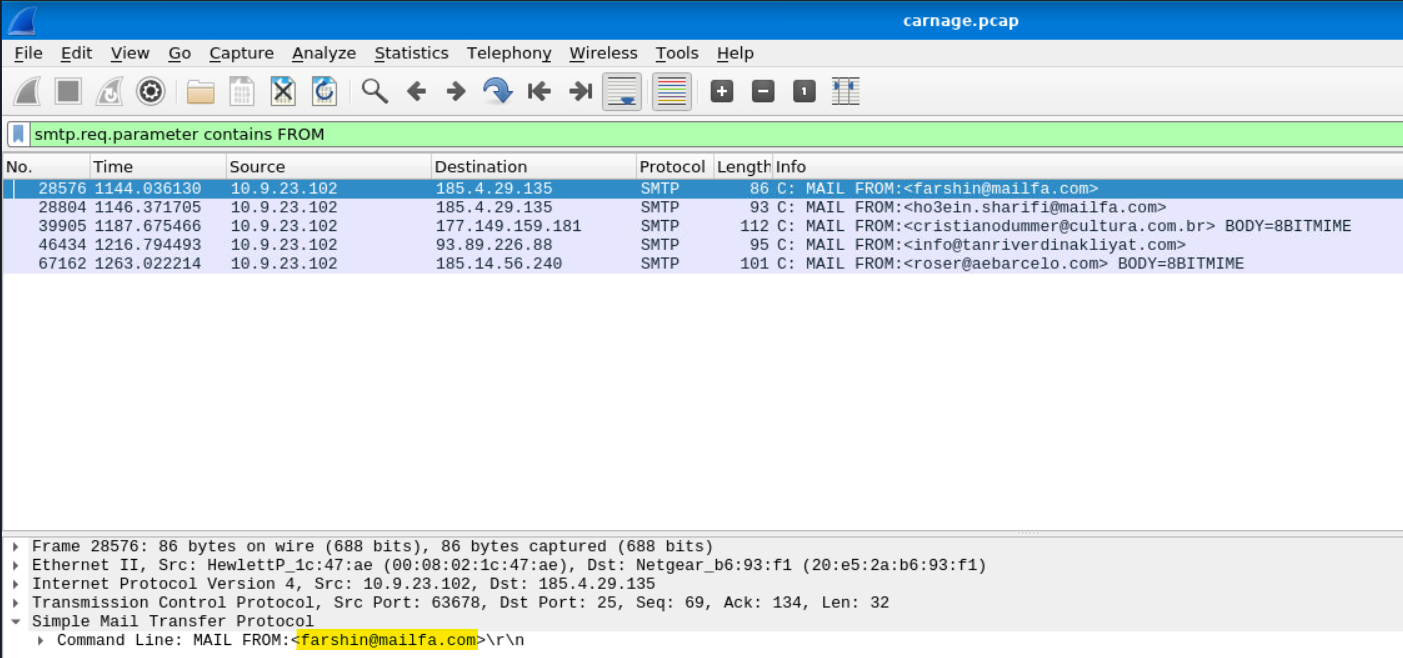
Answer: farshin@mailfa.com
How many packets were observed for the SMTP traffic?
The answer to this can be found by just searching for SMTP traffic.
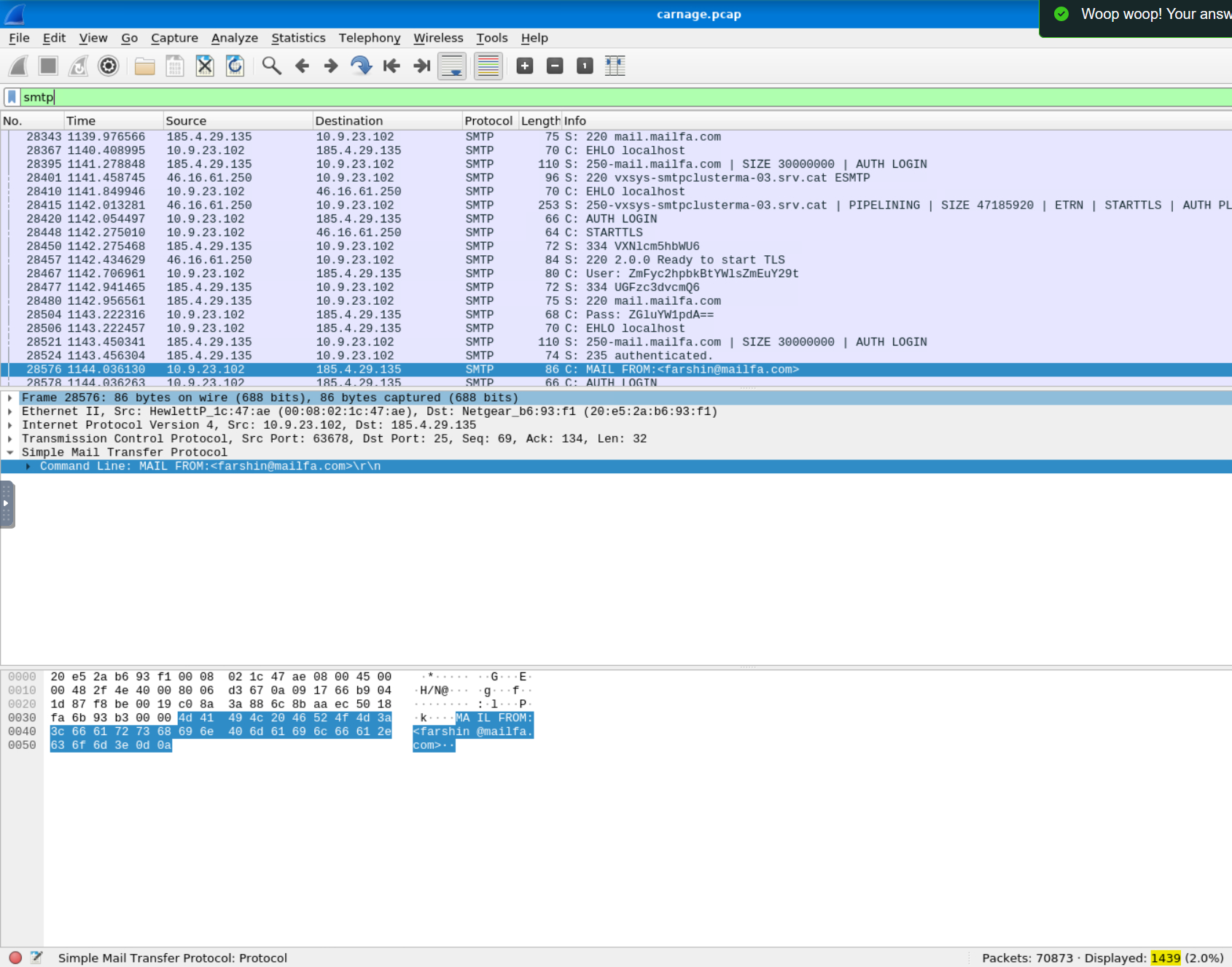
Answer: 1439
