5 min to read
TryHackMe - Friday Overtime - Write-Up
Step into the shoes of a Cyber Threat Intelligence Analyst and put your investigation skills to the test.
The TryHackMe room “Friday Overtime” can be found here.
It’s a Friday evening at PandaProbe Intelligence when a notification appears on your CTI platform. While most are already looking forward to the weekend, you realise you must pull overtime because SwiftSpend Finance has opened a new ticket, raising concerns about potential malware threats. The finance company, known for its meticulous security measures, stumbled upon something suspicious and wanted immediate expert analysis.
As the only remaining CTI Analyst on shift at PandaProbe Intelligence, you quickly took charge of the situation, realising the gravity of a potential breach at a financial institution. The ticket contained multiple file attachments, presumed to be malware samples.
With a deep breath, a focused mind, and the longing desire to go home, you began the process of:
- Downloading the malware samples provided in the ticket, ensuring they were contained in a secure environment.
- Running the samples through preliminary automated malware analysis tools to get a quick overview.
- Deep diving into a manual analysis, understanding the malware’s behaviour, and identifying its communication patterns.
- Correlating findings with global threat intelligence databases to identify known signatures or behaviours.
- Compiling a comprehensive report with mitigation and recovery steps, ensuring SwiftSpend Finance could swiftly address potential threats.
Today we’ll be analyzing some malware samples to identify the malware’s behavior and communication patterns, stepping into the shoes of an analyst named Erica Tracy.
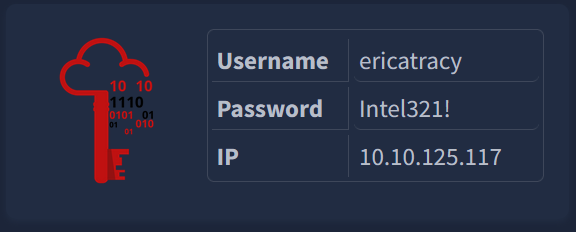
Who shared the malware samples?
We begin by starting the VM and logging into DocIntel platform with the provided credentials…
…and are met with the dashboard.
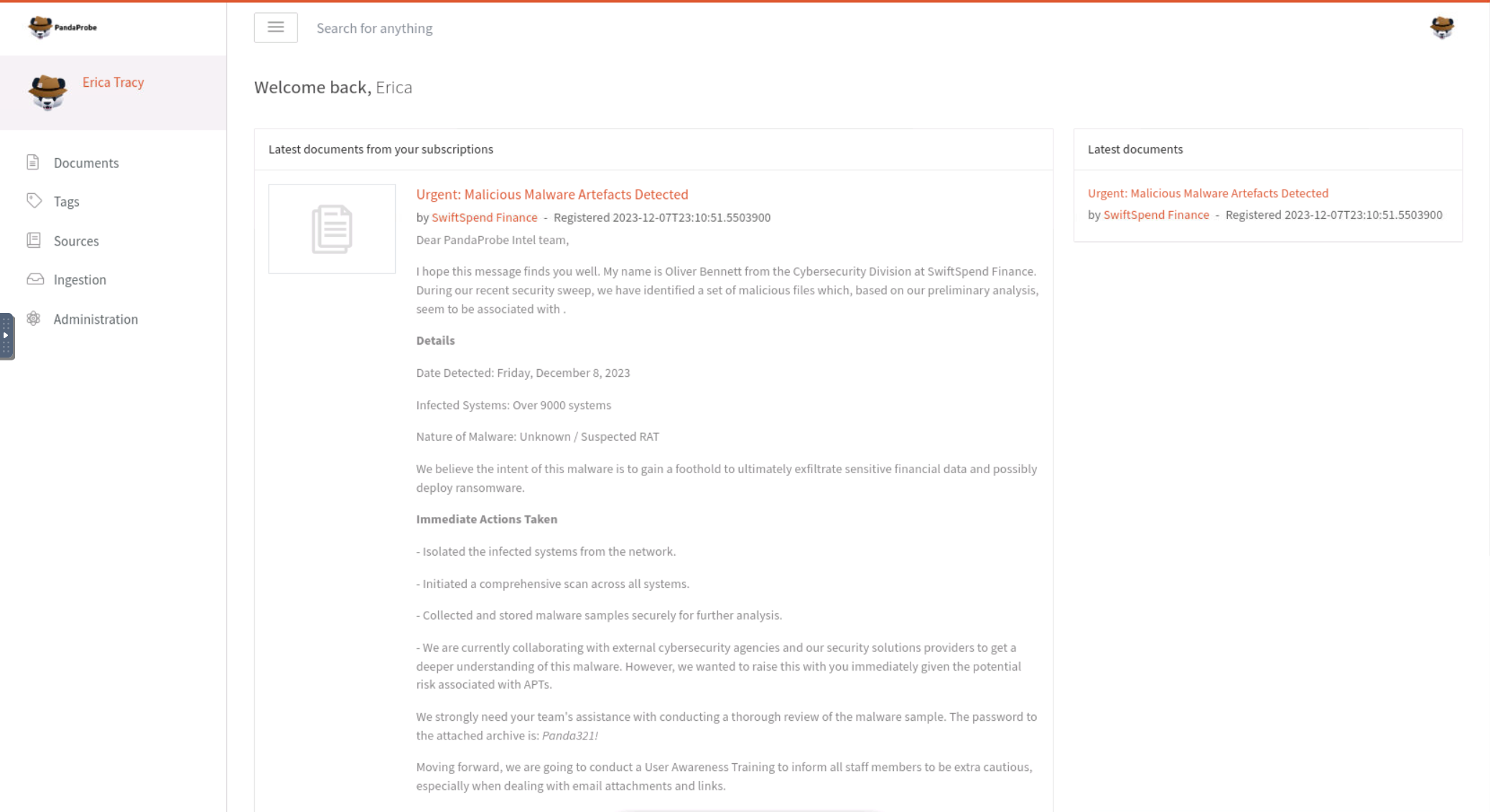
This screen is opened up to a message from a member of the SwiftSpend Finance Cybesecurity Division. His name is our answer!
Answer: Oliver Bennett
What is the SHA1 hash of the file “pRsm.dll” inside samples.zip?
We can open Oliver’s message and download samples.zip to take a look at the suspect files.
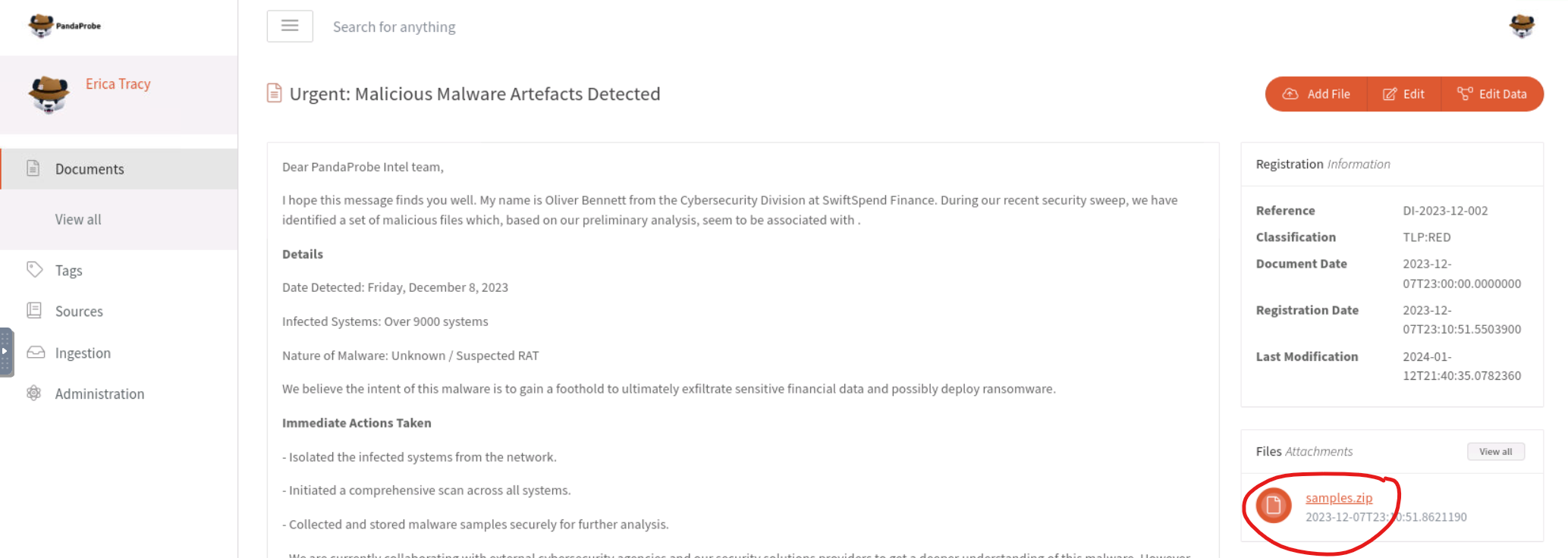
We’ll use our terminal to unzip the archive and move the files to separate directory: samples. The password – Panda321! – was provided by Oliver in his email.
To find the SHA1 hash of pRsm.dll, we can use the sha1sum command on the file.
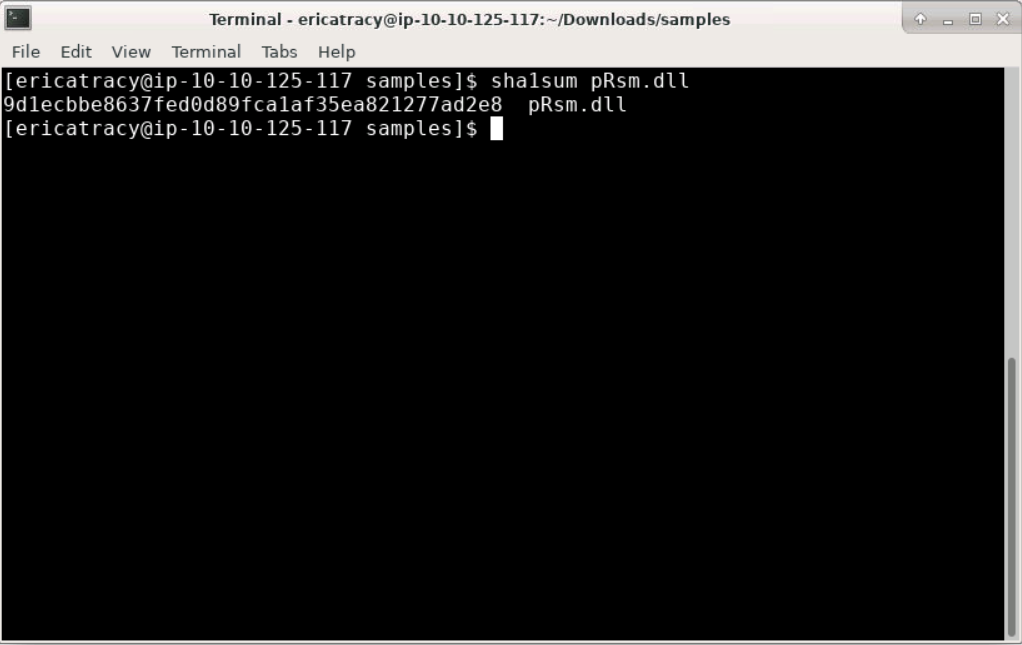
Answer: 9d1ecbbe8637fed0d89fca1af35ea821277ad2e8
Which malware framework utilizes these DLLs as add-on modules?
To find this information, Google is our friend.
This leads us to an article from WeLiveSecurity discussing APT group Evasive Panda in which we can find our answer:
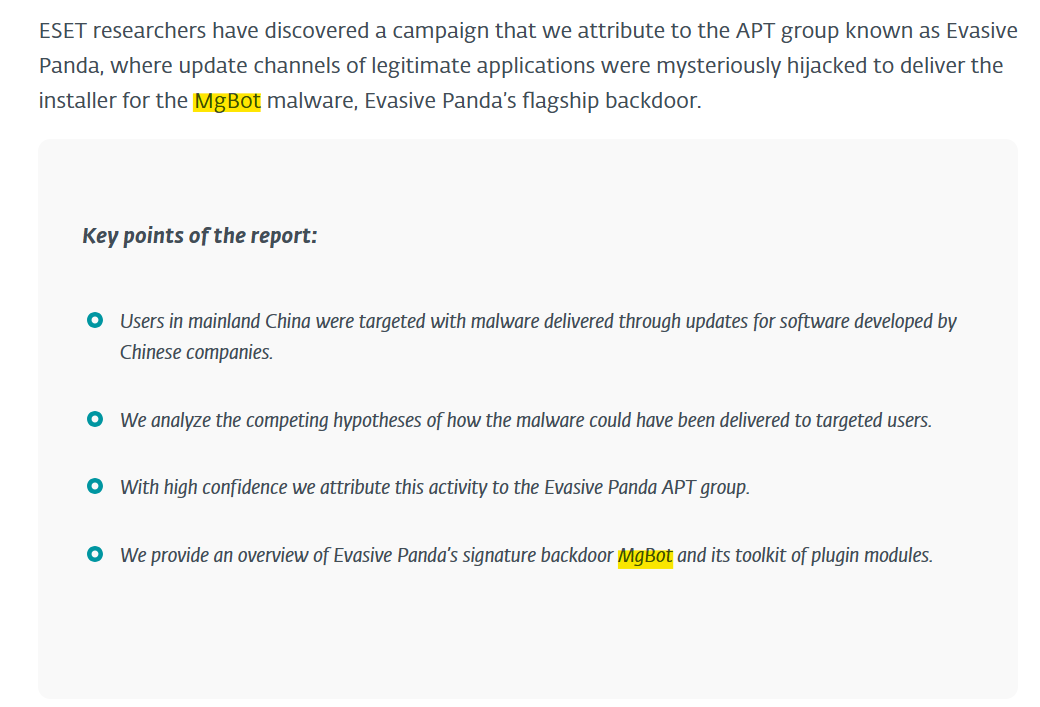
Answer: MgBot
Which MITRE ATT&CK Technique is linked to using pRsm.dll in this malware framework?
The same article from above provides us the answer to this question as well.
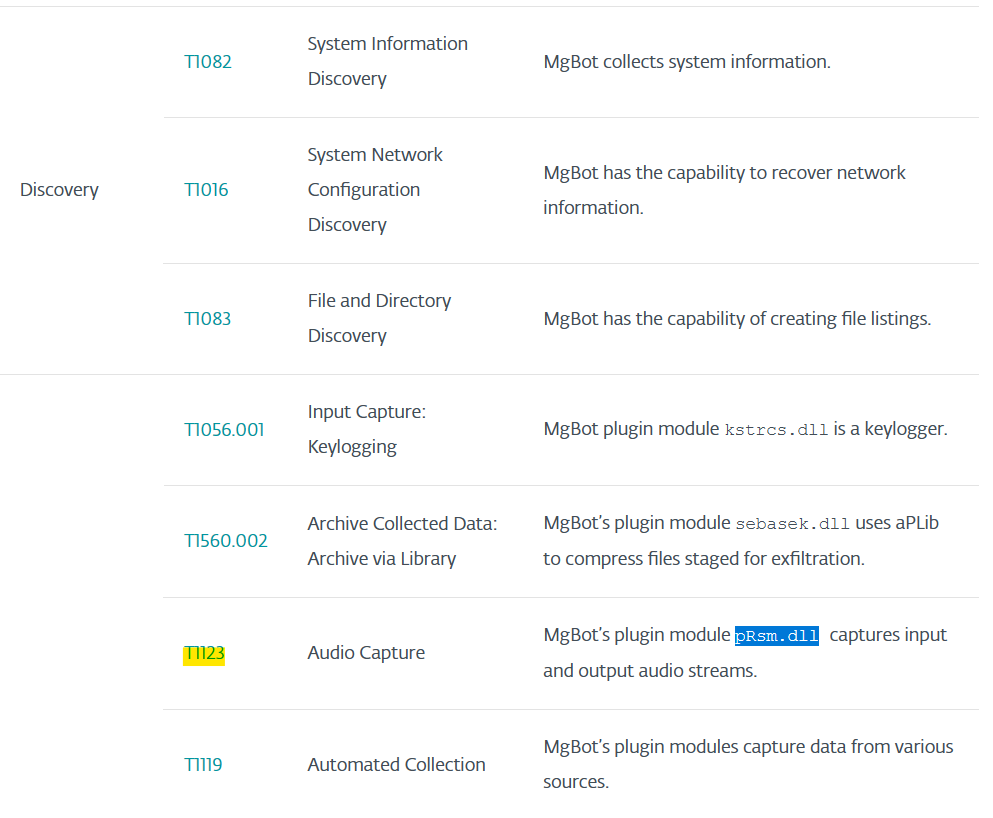
Apparently, pRsm.dll is able to capture audio streams. Spooky.
Answer: T1123
What is the CyberChef defanged URL of the malicious download location first seen on 2020-11-02?
Higher up in the article we find a table containing a URL dated to the same day as in the question:
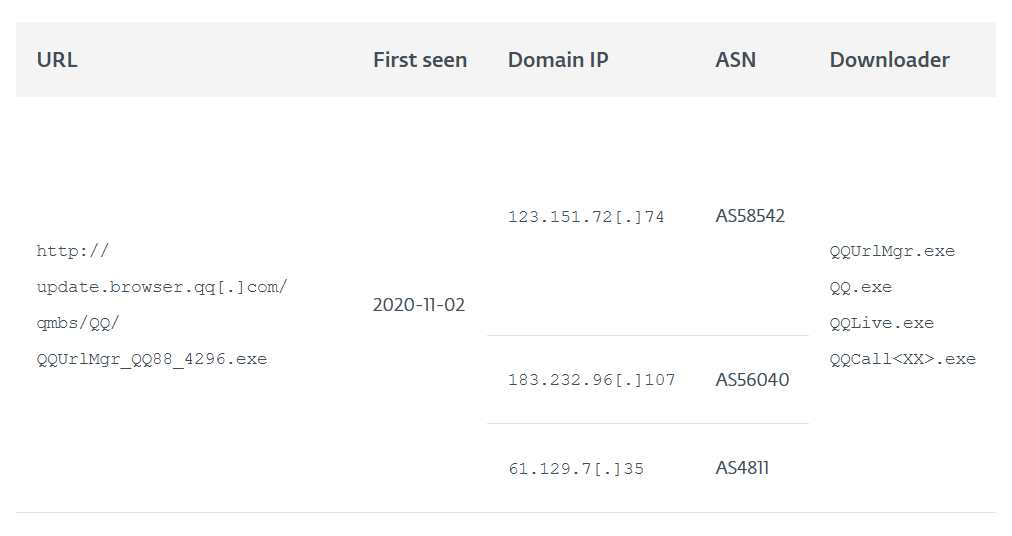
“Defanging” is the process of making a link or address unusable as a clickable item by bracketing off the dots. You can see an above example in the qq[.]com section of the URL.
This allows the address to be shared without running the risk of it being visited and incurring the wrath of whatever terrors may await!
To use CyberChef to do this, we need only to input the URL provided by WeLiveSecurity, add the “Defang URL” recipe, and copy the output.
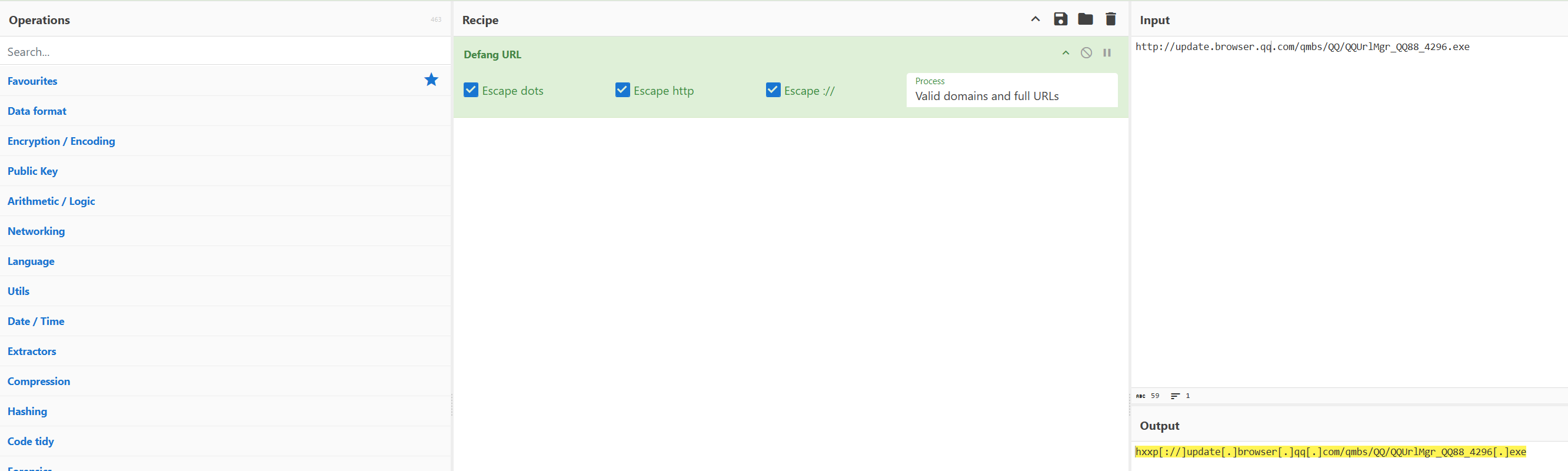
Answer: hxxp[://]update[.]browser[.]qq[.]com/qmbs/QQ/QQUrlMgr_QQ88_4296[.]exe
What is the CyberChef defanged IP address of the C&C server first detected on 2020-09-14 using these modules?
The IP address we’re looking for can be found lower down the article in the Network section:
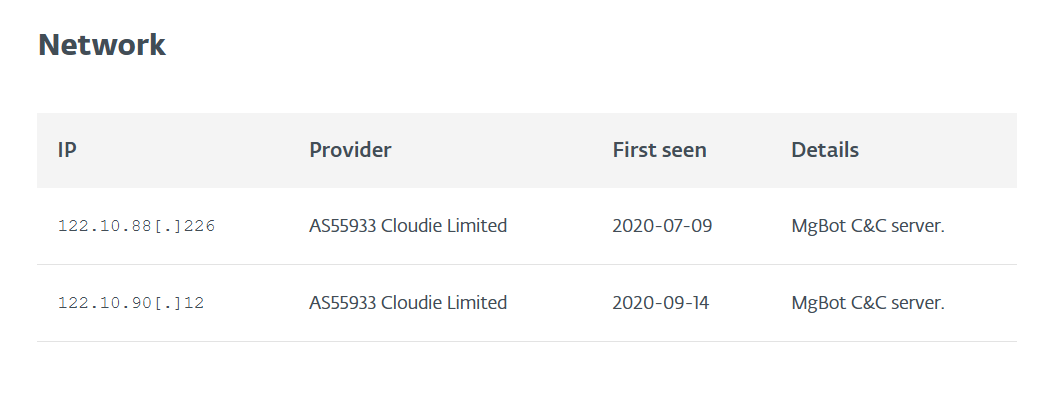
Rinse and repeat for our answer, though we want to switch to “Defang IP Addresses” for this one.
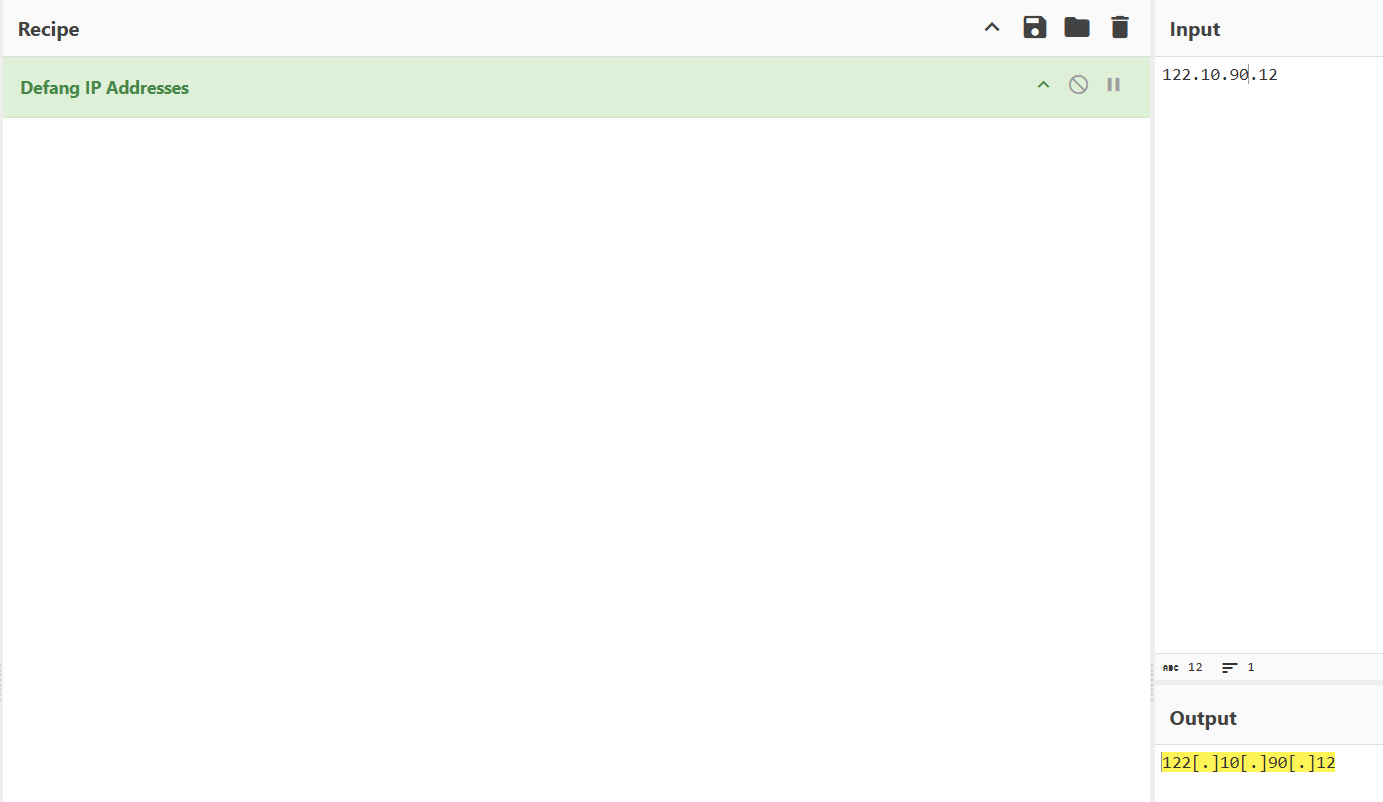
Answer: 122[.]10[.]90[.]12
What is the SHA1 hash of the spyagent family spyware hosted on the same IP targeting Android devices on November 16, 2022?
We’ll visit VirusTotal to find more information about this spyware. We start by searching the IP address from the previous question.
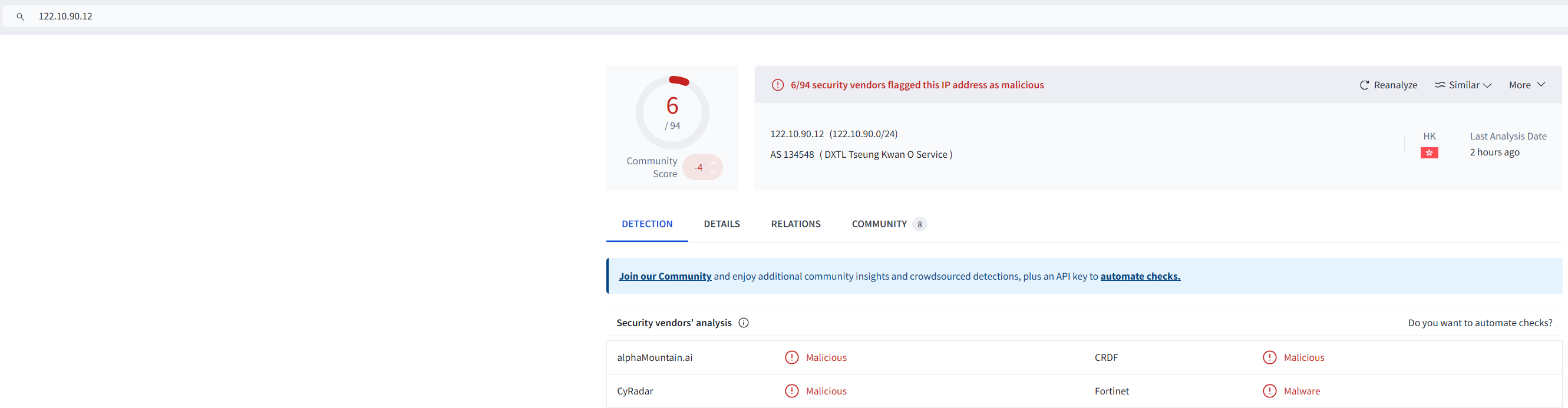
In the Relations tab, under Communicating Files, we find a file with type “Android” that has contacted the IP address in the past. This is our culprit.
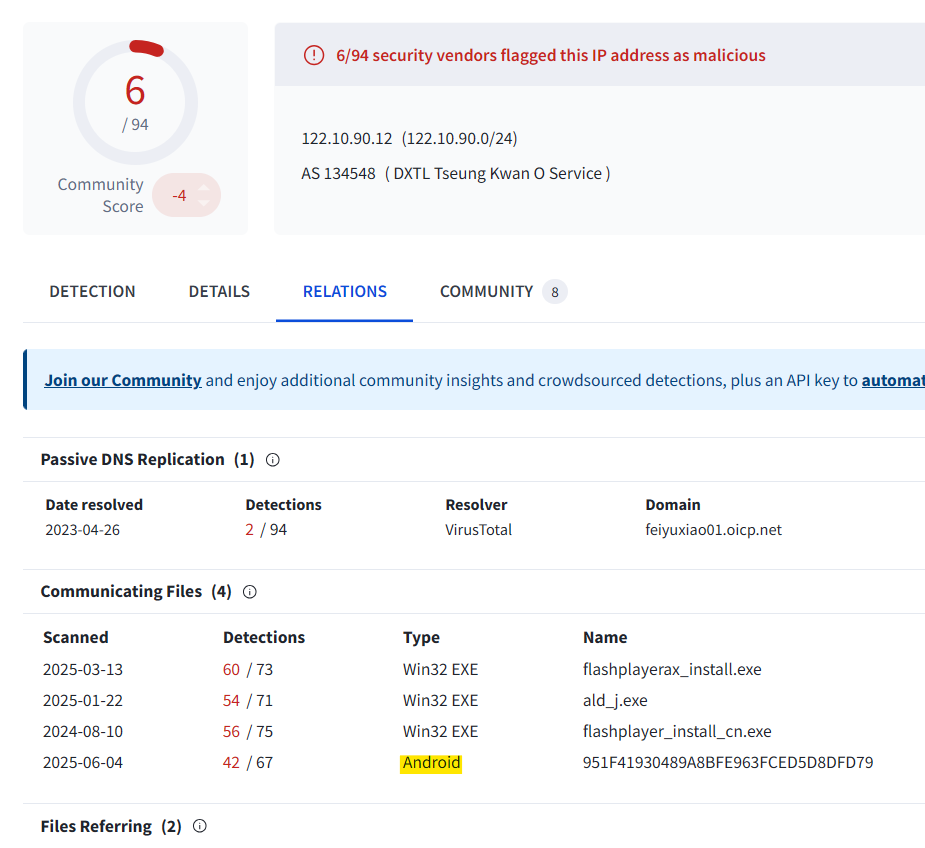
(Note: the Scanned date appears to have been updated since the room was created. Earlier write-ups show that this Android file was once dated at “2022-11-16” – the date referenced in this question. While this is the only Android file for the IP address referenced in VirusTotal, and thus is our likely answer, I was confused as to the discrepancy and thought it important to note.)
Clicking on the file name brings us to a page confirming this is part of the spyagent family.
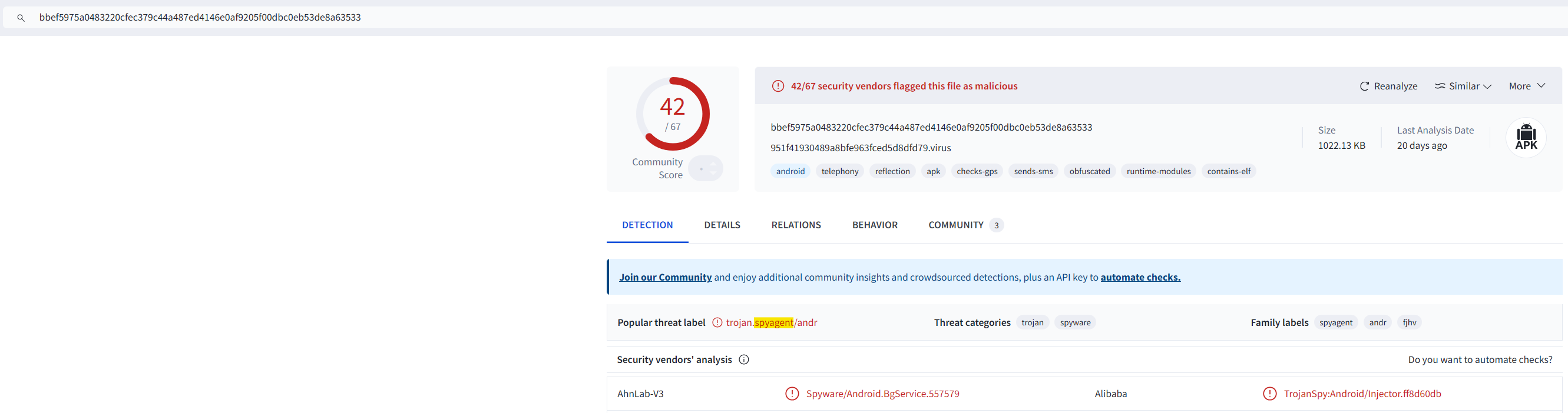
We can then click on Details to grab the SHA1 hash.
Answer: 1c1fe906e822012f6235fcc53f601d006d15d7be
EOF
This room is a good exercise in consulting external research as blue teamer. It also demonstrates the value of groups like ESET Research (WeLiveTraining) discovering and disseminating threat intelligence. Without the likes of such organizations, our character Erica Tracy might have a much harder time identifying the issue at hand!

