4 min to read
TryHackMe - Warzone 2 - Write-Up

The TryHackMe room “Warzone 2” can be found here.
You work as a Tier 1 Security Analyst L1 for a Managed Security Service Provider (MSSP). Again, you’re tasked with monitoring network alerts.
An alert triggered: Misc activity, A Network Trojan Was Detected, and Potential Corporate Privacy Violation.
The case was assigned to you. Inspect the PCAP and retrieve the artifacts to confirm this alert is a true positive.
This room is a follow-up to “Warzone 1”. Let’s get started!
What was the alert signature for A Network Trojan was Detected?
We begin by opening the provided .pcap file in Brim…
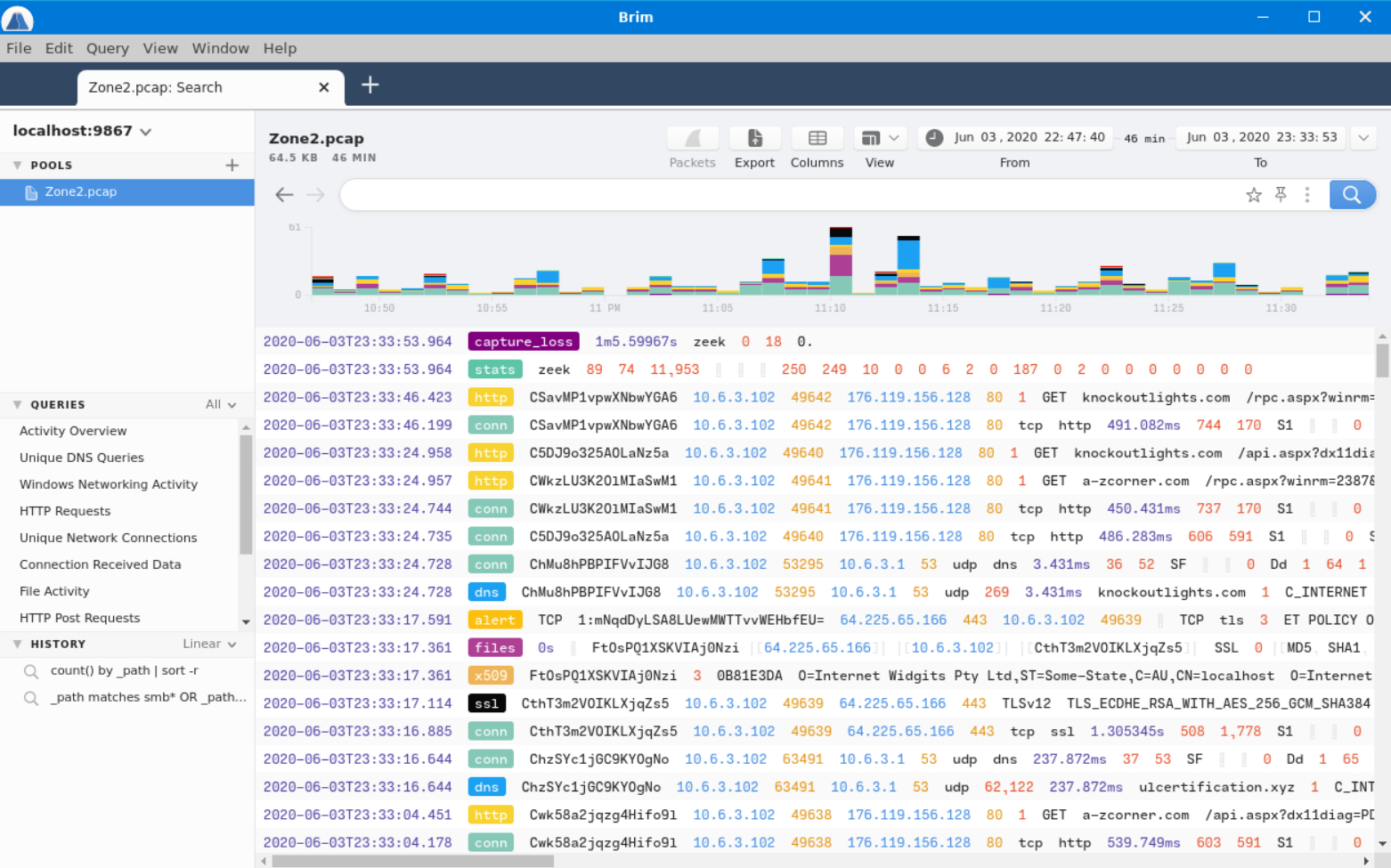
…and searching the phrase “A Network Trojan was Detected”.
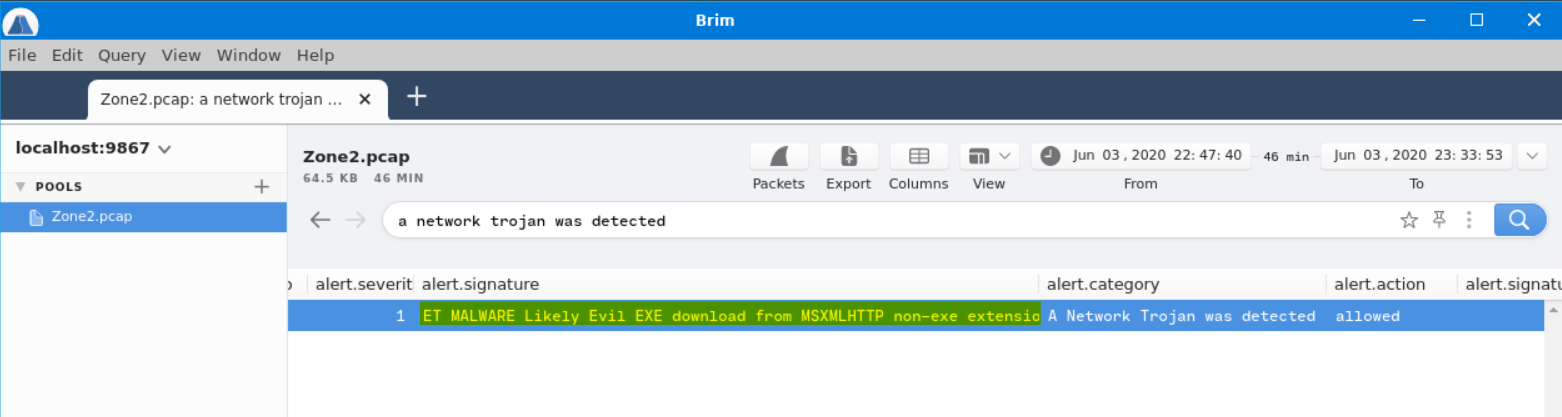
Answer: ET MALWARE Likely Evil EXE download from MSXMLHTTP non-exe extension M2
What was the alert signature for Potential Corporate Privacy Violation?
We rinse and repeat to find this answer.
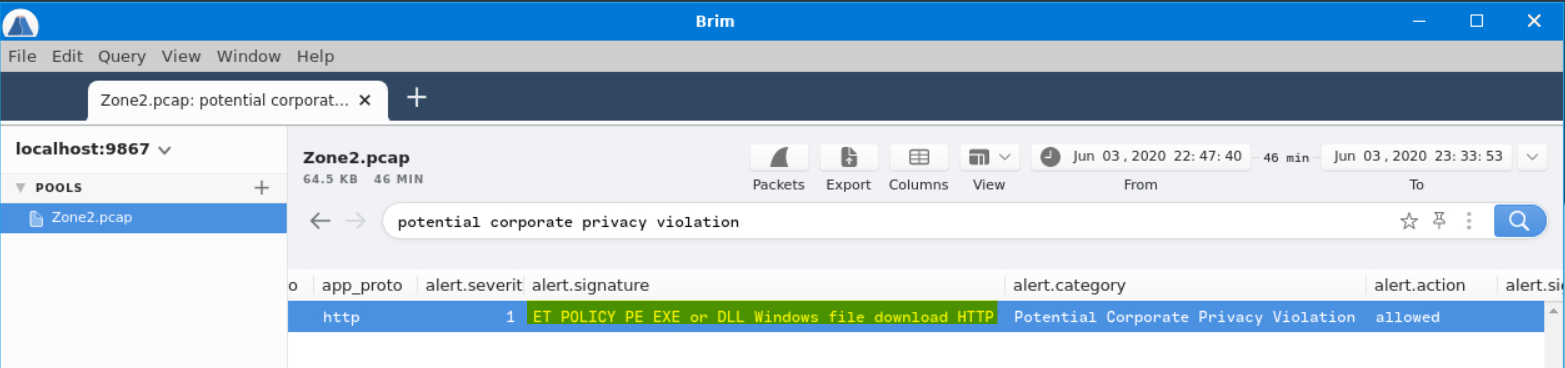
Answer: ET POLICY PE EXE or DLL Windows file download HTTP
What was the IP to trigger either alert? Enter your answer in a defanged format.
For a cleaner look at the info, we’ll open the Brim Log Detail window by double-clicking the alert.
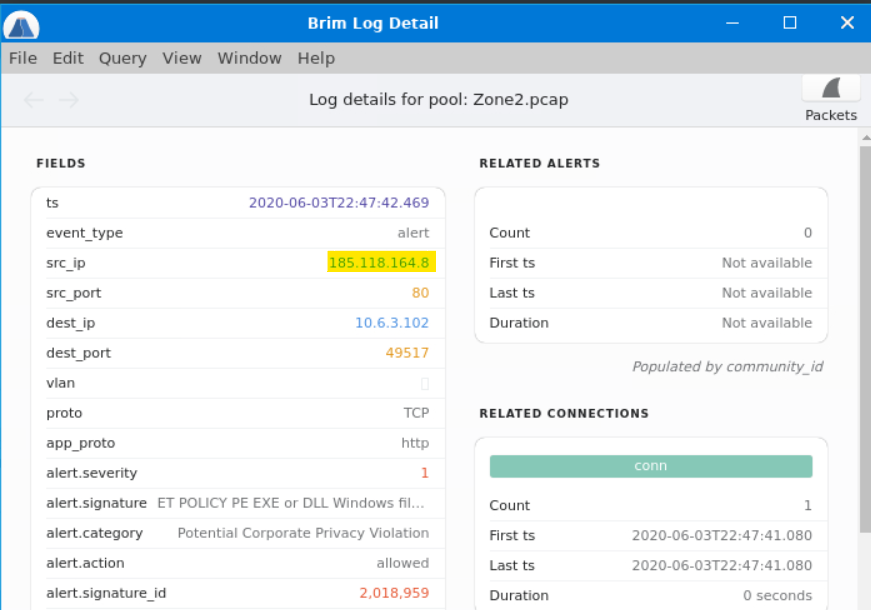
In the src_ip field we find our answer. We can then defang the IP address by using CyberChef.
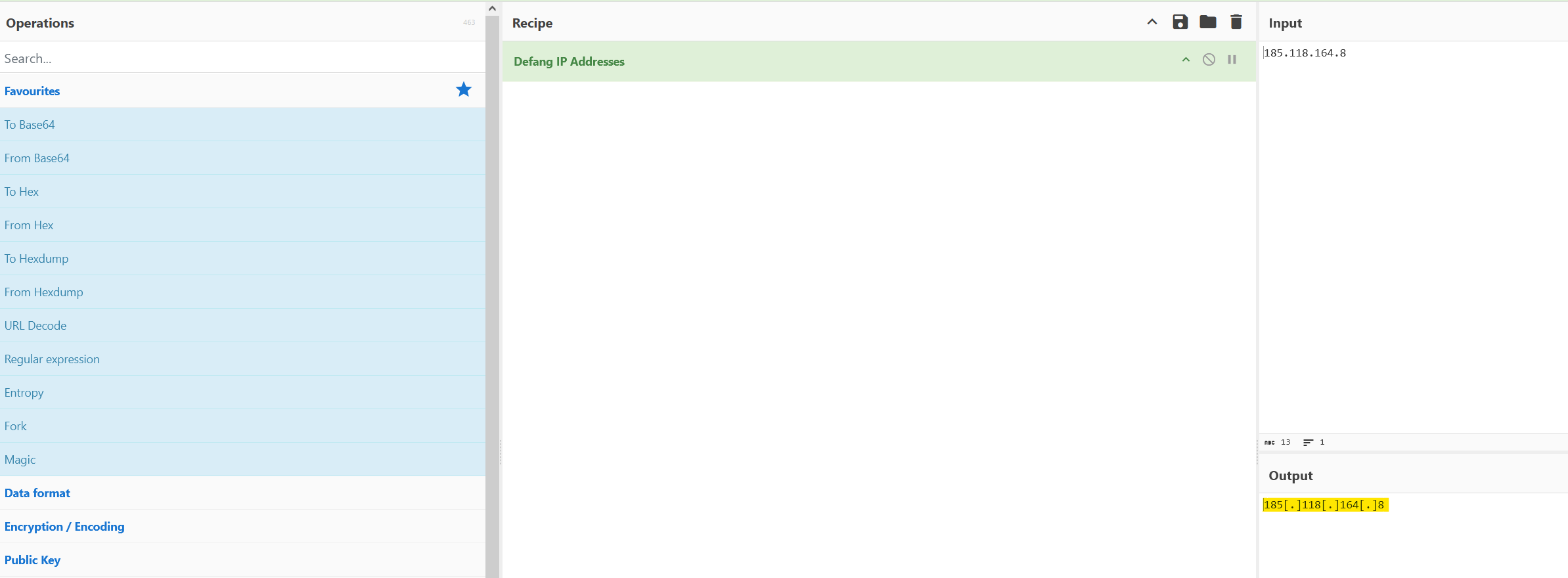
Answer: 185[.]118[.]164[.]8
Provide the full URI for the malicious downloaded file. In your answer, defang the URI.
I found the answer to this question by clicking on “File Activity” under “Queries”…
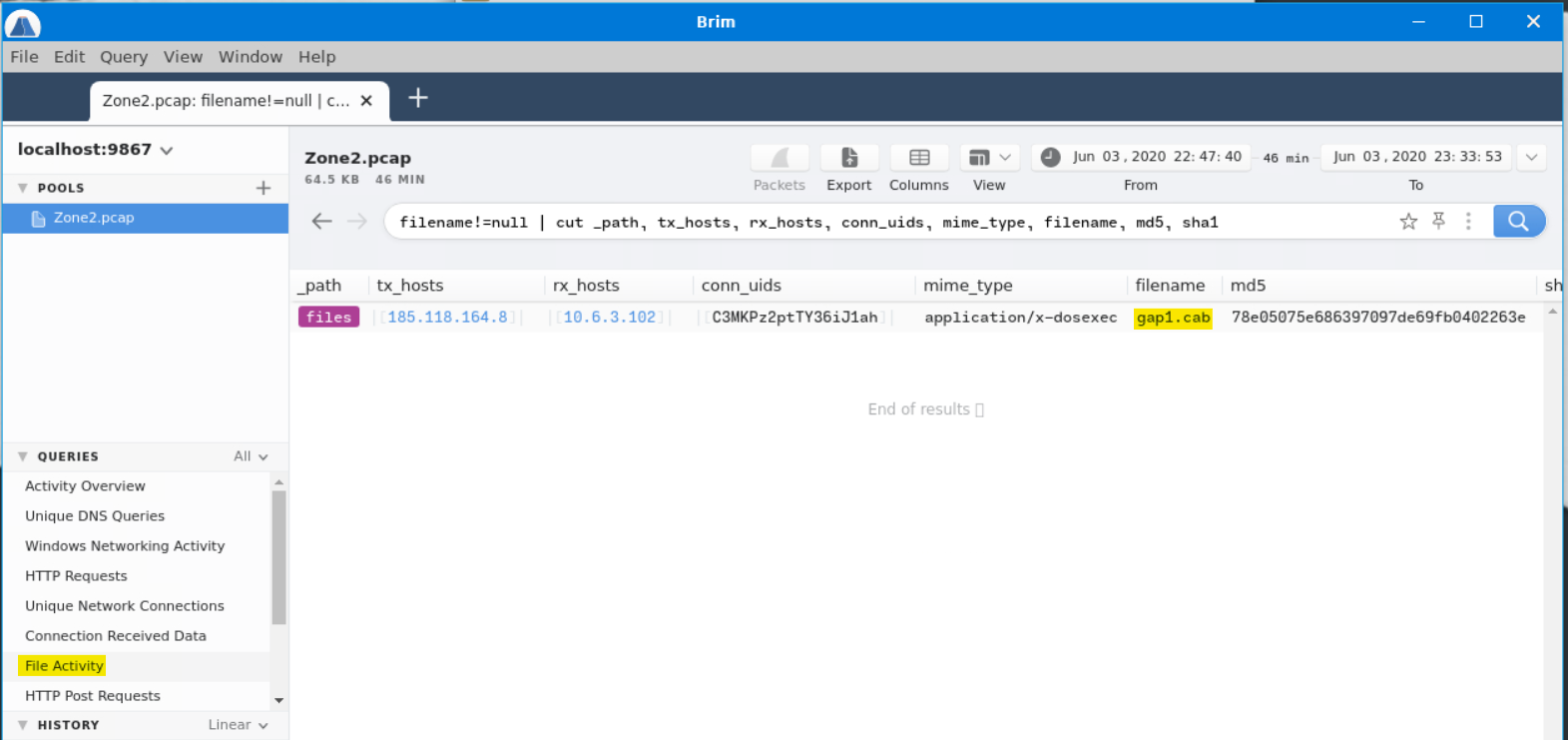
…which brought me to the filename: gap1.cab.
I then searched for references to that name in the .pcap file.
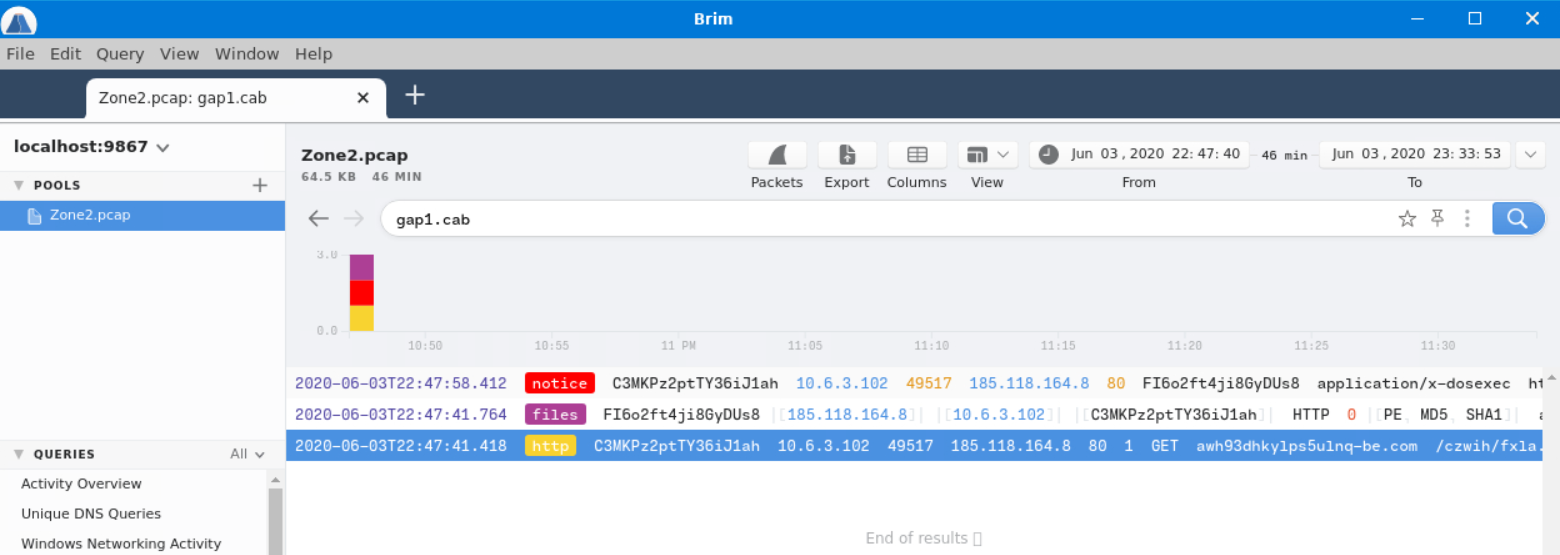
We’re looking for the full URI of the downloaded file, so I opened the http packet in more detail.
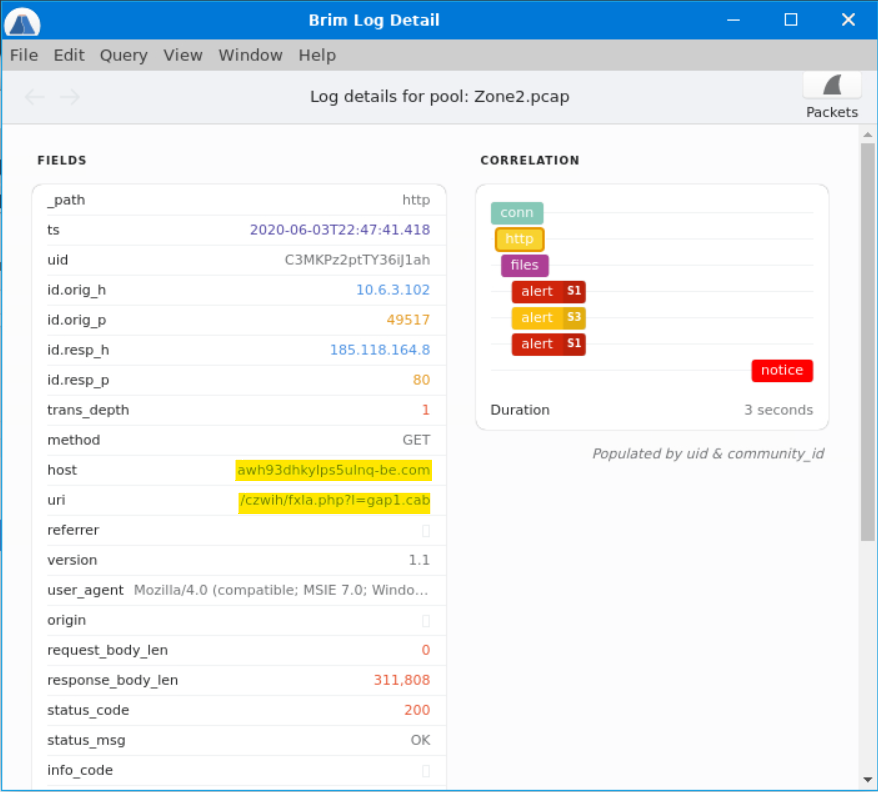
We can see host and uri fields in the Detail window. Combining these two fields gets us our answer. CyberChef can once again defang (or we can do it ourselves).
Answer: awh93dhkylps5ulnq-be[.]com/czwih/fxla[.]php?l=gap1[.]cab
What is the name of the payload within the cab file?
To find this answer, we start by going back to the search for gap1.cab and selecting the files packet.
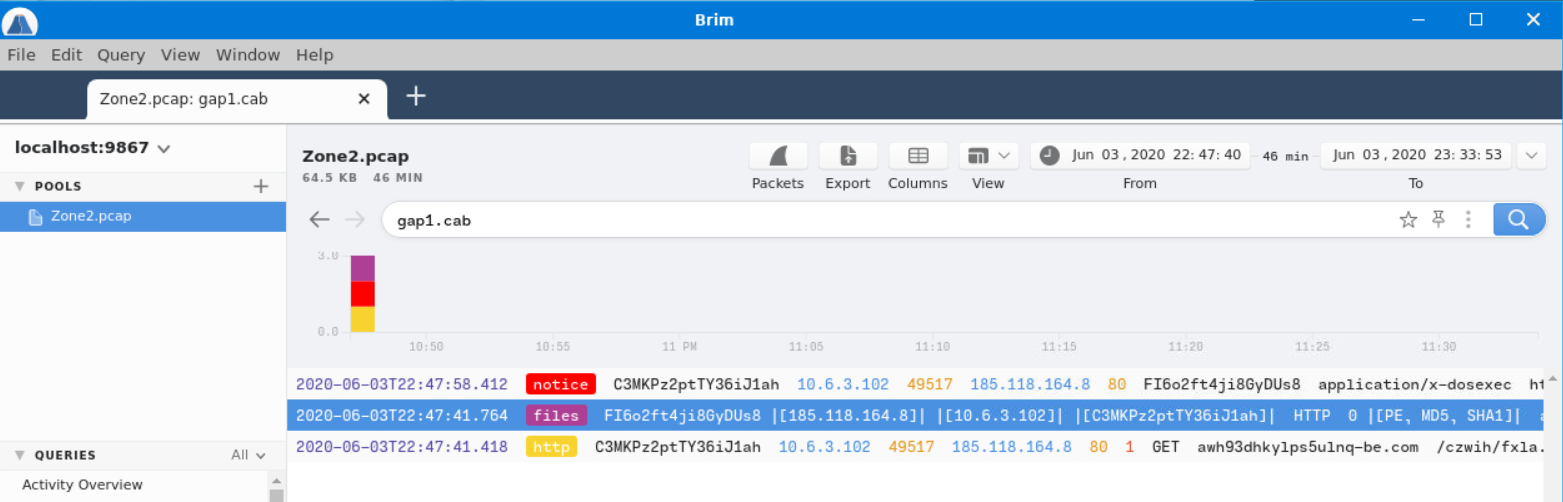
We pull the MD5 hash so we can put it into VirusTotal and learn what’s been uncovered about this file.
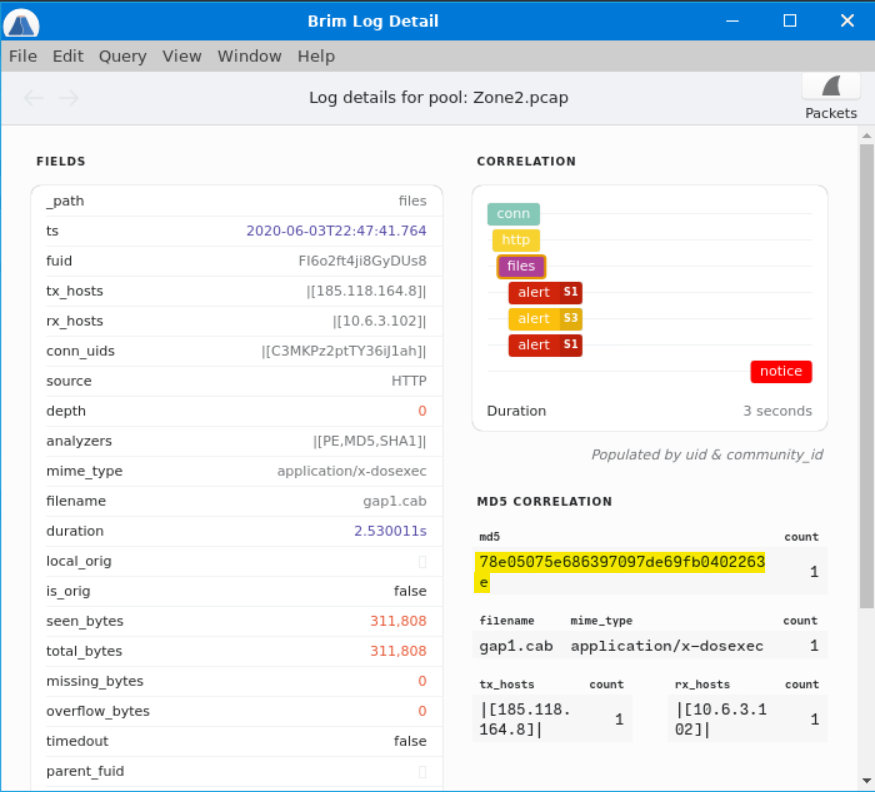
Putting the hash into VirusTotal, we find the name of the payload.
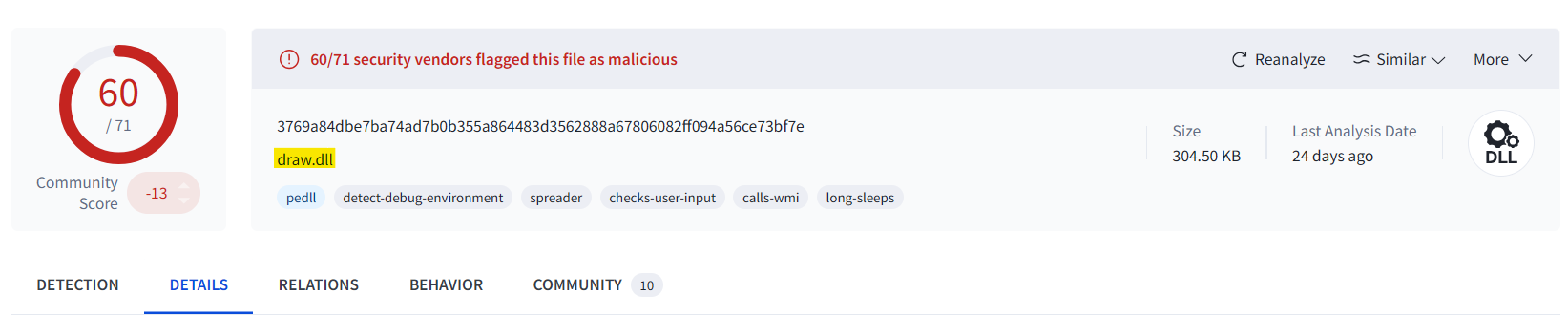
Answer: draw.dll
What is the user-agent associated with this network traffic?
Returning back to the details for the http packet, we can check the user_agent field for the answer to this question.
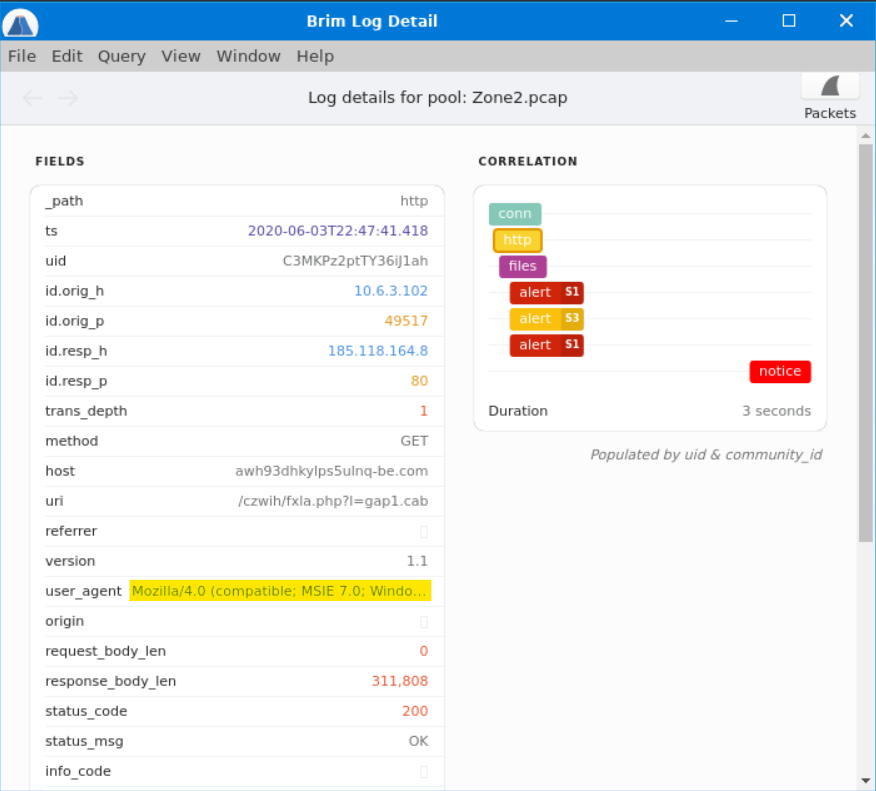
(Interesting that this feels like it was asked out of sequence.)
Answer: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; WOW64; Trident/8.0; .NET4.0C; .NET4.0E)
What other domains do you see in the network traffic that are labelled as malicious by VirusTotal? Enter the domains defanged and in alphabetical order. (format: domain[.]zzz,domain[.]zzz)
We never checked the “Misc activity” alerts, so let’s investigate those.
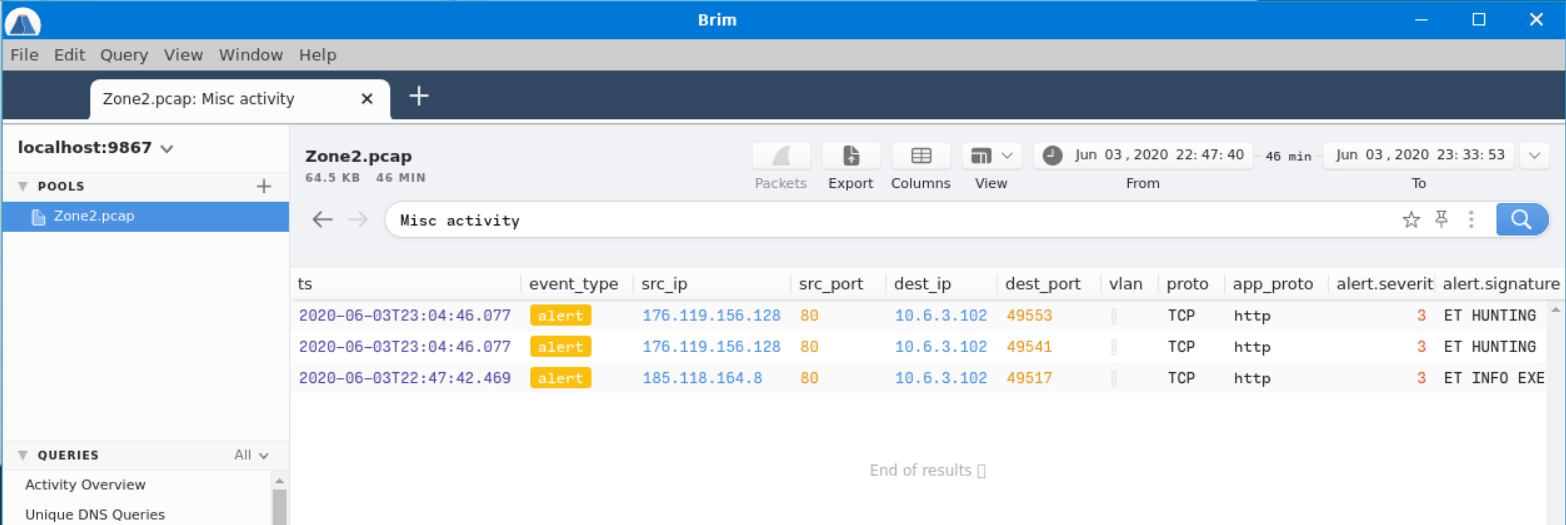
In doing so, we’re presented with two source IP addresses, one of which we’re already familiar with. Let’s look for more packets related to the 176[.]119[.]156[.]128 address.
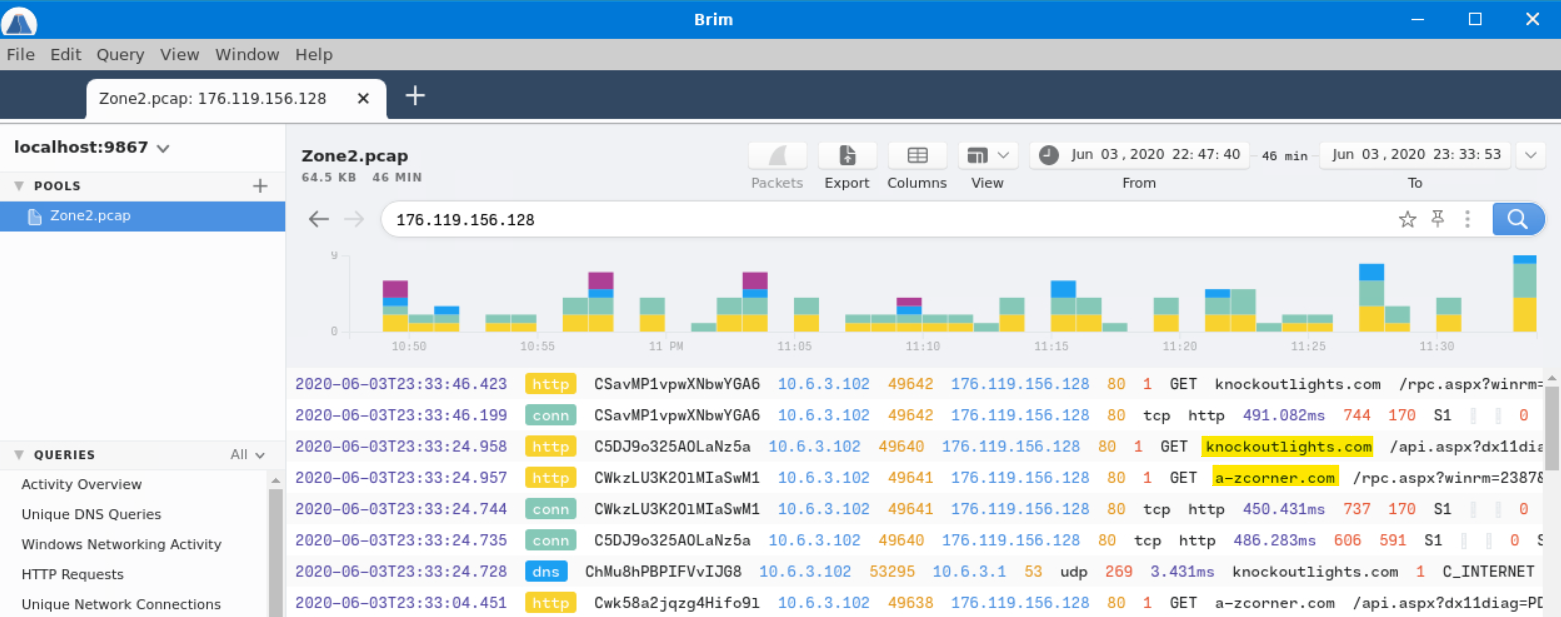
In doing so, we see two domains keep popping up. These are most likely our answers, but let’s confirm this on VirusTotal.
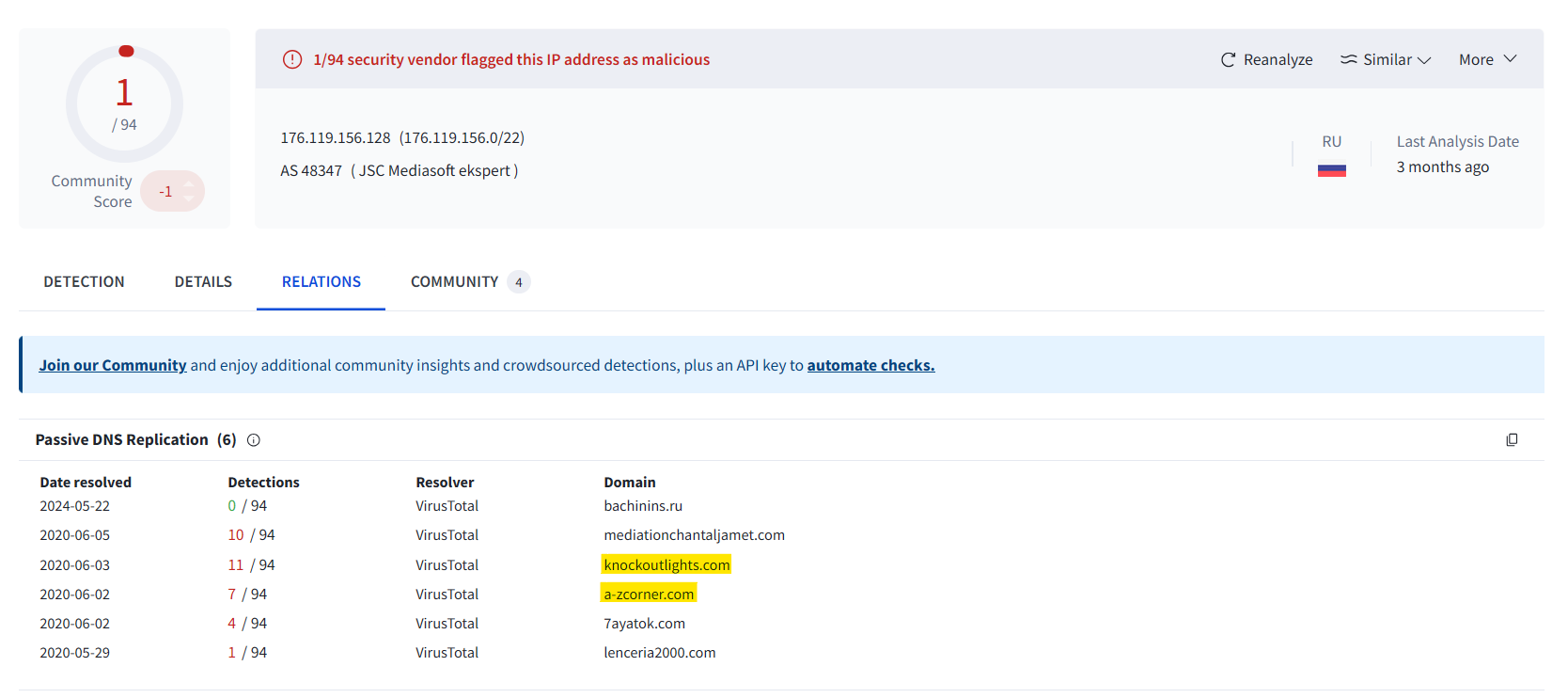
There we go! Once again, CyberChef will defang for us.
Answer: a-zcorner[.]com,knockoutlights[.]com
There are IP addresses flagged as Not Suspicious Traffic. What are the IP addresses? Enter your answer in numerical order and defanged. (format: IPADDR,IPADDR)
I like the title “Not Suspicious Traffic”. Immediately sounds suspicious to me, though I suppose we can take it at its word.

We can find this traffic by searching alert.category == "Not Suspicious Traffic". This gives us the two IP addresses.
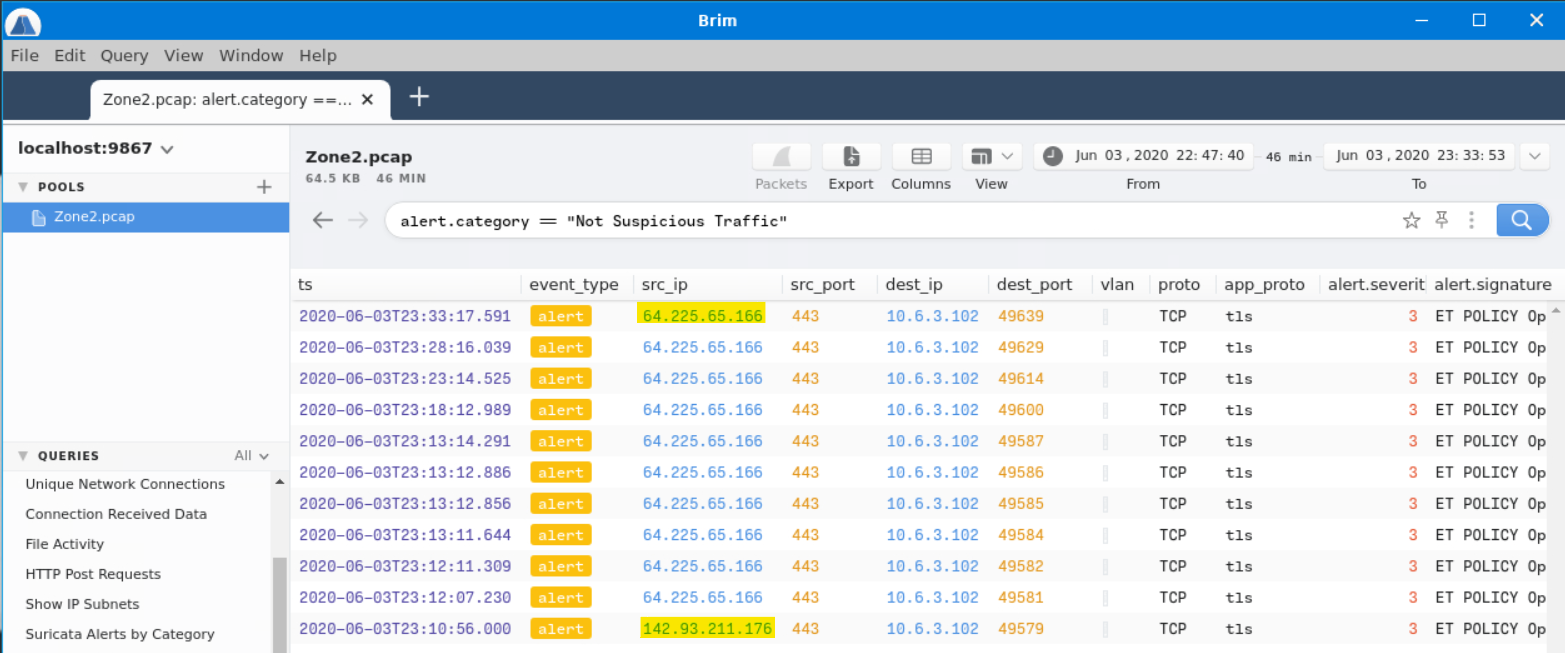
CyberChef can defang.
Answer: 64[.]225[.]65[.]166,142[.]93[.]211[.]176
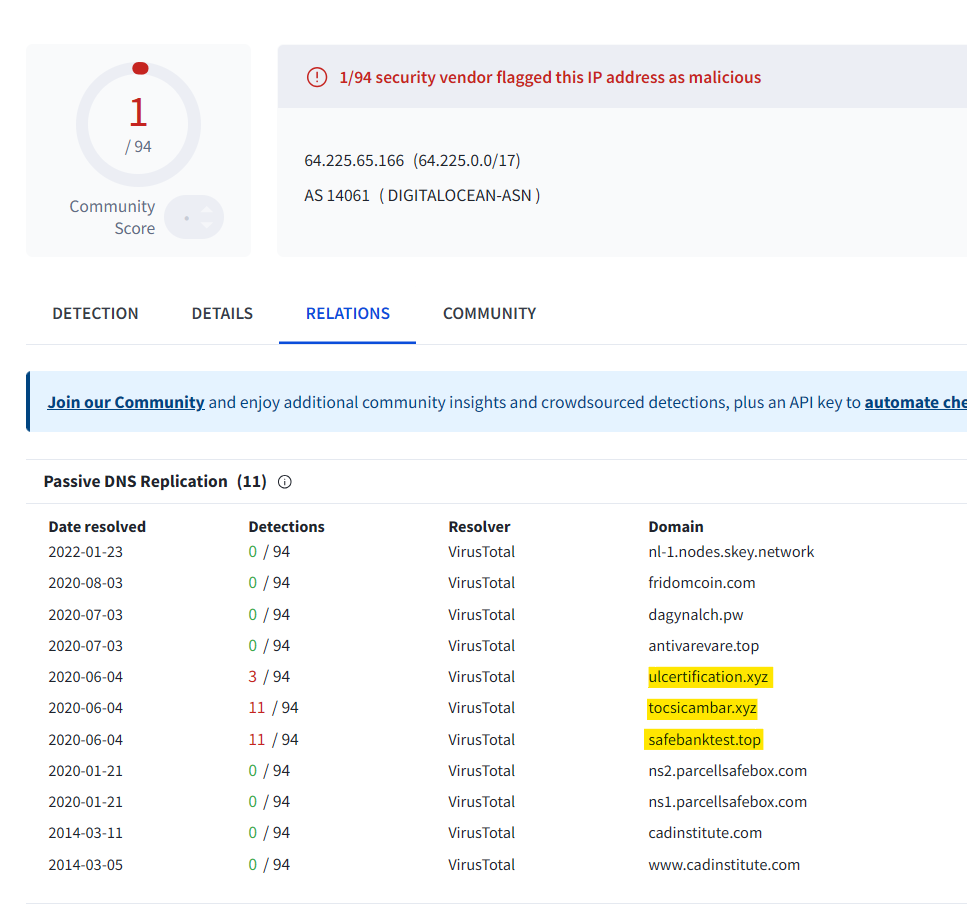
For the first IP address flagged as Not Suspicious Traffic. According to VirusTotal, there are several domains associated with this one IP address that was flagged as malicious. What were the domains you spotted in the network traffic associated with this IP address? Enter your answer in a defanged format. Enter your answer in alphabetical order, in a defanged format. (format: domain[.]zzz,domain[.]zzz,etc)
We can find a list of contacted domains by searching _path=="ssl" | id.resp_h==64.225.65.166 | by server_name | sort server_name.
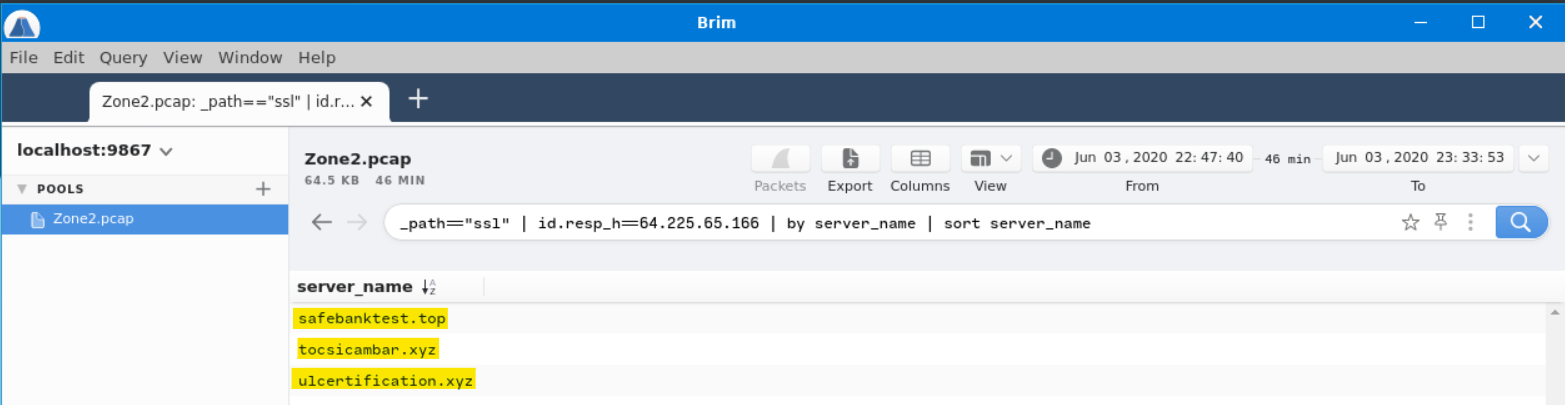
We can corroborate this in VirusTotal.
CyberChef defangs for us.
Answer: safebanktest[.]top,tocsicambar[.]xyz,ulcertification[.]xyz
Now for the second IP marked as Not Suspicious Traffic. What was the domain you spotted in the network traffic associated with this IP address? Enter your answer in a defanged format. (format: domain[.]zzz)
We can run a similar query on the second IP to get our answer.
Answer: 2partscow[.]top
EOF
Another quick exploration of suspicious traffic in Brim. I really like this tool – it’s fun to be able to parse through packet captures in such a nice GUI.
Tools used: Brim
